Oktane20: Roadmap - Security
Transcript
Details
Tomar Mayara: Hello everyone. Thank you for joining Oktane20 Security Roadmap. We are excited to be here even if it's virtually, and we really appreciate you joining us today. Before we begin, little bit of legal. As you know, Oktane is a public company and so we are flagging that any forward looking statements we share here are subject to change. Feel free to read the Safe Harbor note, in depth at your own leisure. All right. So I'm Tomar Mayara, Group Product Manager for the security products team. Thanh-Ha.
Thanh-Ha Nguyen: And I'm Thanh-Ha Nguyen, Product Manager for the security products team.
Tomar Mayara: Before we begin, if you're watching it live, please open the Q&A tab and ask any questions you might have during the presentation. Our team is here to answer all your questions live. We have a lot to share with you today. But before we dive into talking about the shiny new things, we want to share some stories from 2019.
Tomar Mayara: In Oktane19, last year, we launched risk scoring on the keynote stage. With risk scoring on every app login, Oktane looks at the context around the login, such as user location, device, and even network, and evaluates that against the previous logins that Okta has seen. If the login is very different for that user, then the risk may be evaluated as high. If the login is similar to previous logins, we will evaluate the log in as low. Admin can create policies around this risk scoring. For example, users that always log in from the same IP, the same location, same device, might be considered as low risk. Risk scoring allows admin to more securely evaluate the context around login and lower friction. The feature is going GA in May this year, and we are excited to see how we use it.
Thanh-Ha Nguyen: Last year, we made major investments in unlocking passwordless log in experiences for your organizations and applications. While passwordless is still relatively new in the industry, we've actually had various forms of passwordless in Okta from the early days. Users have been able to log in passwordlessly from 80 joint machines using our desktop SSO feature. Other customers have been using PIV and smart cards to log in without a password. And you've been able to log in passwordlessly using device trust via EMM integrations.
Thanh-Ha Nguyen: In 2019, we introduced even more passwordless options with the release of WebAuthn and factor sequencing. With WebAuthn, users could use security keys or platform authenticators such as Windows Hello or Mac Touch ID for secure phishing-resistant authentication. By combining WebAuthn with factor sequencing, admins could define the chain of factors for a user to log in.
Thanh-Ha Nguyen: Last but not least, for seamless customer authentication, we added support for email magic link. With this feature, customers can log in seamlessly via just a click in the links in an email. All of these investments together, again, moved us forward in providing stronger authentication methods, while lowering friction as much as possible for our users. Okay. Back to you Tomar.
Tomar Mayara: We also launched ThreatInsight, Okta threat detection and response too. ThreatInsight aggregates data across all our customers. It then applies patterns to detect credential-based attacks. For example, [inaudible 00:03:54] We then identify the IPs that are involved in these attacks and mark these IPs as suspicious. When a request comes into your [inaudible 00:04:03], we can check if the IP is suspicious. If it is, then we can block the access. If it's not, then the request goes through the usual policy validation. ThreatInsight was released to GA about eight months ago, and since then we have seen around 4,000 production olds that have enabled this feature. About 60% of it in on block code to automatically block or suspicious IPS detector. Finally, about 30 million suspicious events ever detected in February, 2020 alone. Thanh-Ha back to you.
Thanh-Ha Nguyen: To tie it all together in 2019, we also released HealthInsight. HealthInsight provides personalized recommendations based on your orgs current configurations based on best practices for how best to secure your org. We intend Health Insight to be the place to go for admins, to learn about new features in Okta and how to use them. Today health Insight notifies you if you have not yet enabled features like Threat Insight, security email notifications, and common password detection. Health Insight was generally available starting in January and should be available from everyone's admin dashboard today. You might've seen it already. Back to Tomar.
Tomar Mayara: We've spent a lot of time last year, talking to you about customers. We want to make sure that everything we build solve a real pain point and remove the needle in a meaningful way. Here's what we've heard.
Tomar Mayara: First admins are required to deal with increasingly complex use cases. This means more users, more apps and more resources to protect. Okta is investing in simplifying policy management while we are also making sure that it's flexible and powerful enough to meet your needs.
Tomar Mayara: Second customers are looking at Okta for help mitigating threats. We definitely hear you on that. And we keep evolving our threat insight products.
Tomar Mayara: Last customer's looking for ways to lower [inaudible 00:06:21] cost. We will discuss how we help your users to self service instead of calling the desk.
Tomar Mayara: From here, we'll go through each of these categories and we'll discuss the product investments we are making this year to help you, our customers. Thanh-Ha.
Thanh-Ha Nguyen: Let's start with what we're building to simplify policy management.
Thanh-Ha Nguyen: In 2019, we heard that admins today have more apps than ever before. According to Okta is 2020 businesses at work report orgs have on average 88 apps per org. Every time an app is added, admins are required to create new policies for that specific app. As org scale to tens hundreds, or even thousands of apps, ongoing management integration and new features and policy audits can be difficult. With Oktas identity engine features we can help you really simplify this management. We can give you the ability to link multiple applications to the same policy. You create the policy once and apply it to all apps sharing the same requirements. For example, if you see on the screen right now, we've created one policy with one factor login password lists for everyday apps that a user might log into.
Thanh-Ha Nguyen: However, for highly sensitive apps, we can create another policy requiring strong MFA, such as security keys to protect apps that hold especially sensitive data for any new apps you add, you can simply add the app to an existing policy and they'll apply like that. The identity engine also unlocked another use case that we've heard from many admins today.
Thanh-Ha Nguyen: Today, the majority of our workforce customers set a default Okta sign in policy requiring two factor authentication to every log into Okta. This means that no matter what app an user is accessing box, get hub, or even just the lunch menu app, they are prompted for password and a second factor when they log in. This can be burdensome for users who just simply want to access some data very quickly. What we've heard from you is that you actually want to match the authentication requirements to the sensitivity of the app. Only step up a user when they access critical data.
Thanh-Ha Nguyen: Okta Identity Engine helps admins unlock this use case. If a user is logging into a noncritical app, let's take that lunch menu app as an example, admins can set policies to minimize authentication requirements. Perhaps one factor passwordless login. When the user goes to access more sensitive applications, admins can separate set a separate policy for these apps to make sure that users are authenticating with the required multifactor. By setting an evaluating authentication requirements on a per app basis admins can make sure that authentication assurance on the login matches the sensitivity of the app. All the while admins can lower friction for end users in every other use case.
Thanh-Ha Nguyen: Speaking of passwordless authentication, as we announced at the keynote this year, we're launching Okta FastPass, Okta FastPass allows users to get passwordless logins to any Okta managed app. This is done by registering devices to universal directory using Okta verify. Once the device is registered FastPass will verify that the device is registered with the user upon every login optionally admins can set policy to check user contexts like network as well as if the device is managed. If everything looks secure the users will not be prompted for any credentials. There is no app switching required to ensure a seamless login for the end user. Optionally, if required in policy FastPass may also prompt for step up with pin or biometric on the user's device for additional user verification. If you haven't already seen in action, check out our keynote demos and learn about it in more detail in the devices roadmap session.
Thanh-Ha Nguyen: Of course, Okta verifies only one of the many factors that users use to authenticate to Okta today. This is why last year we launched our factor sequencing features so that you can define any factor chain for users authenticated to Okta. When talking to customers about using factor sequencing in the last year, we found that most of the use cases were centered around achieving desired security outcomes or reaching a specific authentication assurance before a user can access a resource. For example, require authentication with at least one strong phishing resistant factor, like WebAuthn meeting a specific NIS guideline on authentication assurance, prompting the user for any one of their enrollment factors or only prompting for MFA. If the user is enrolled in an additional authentication factor.
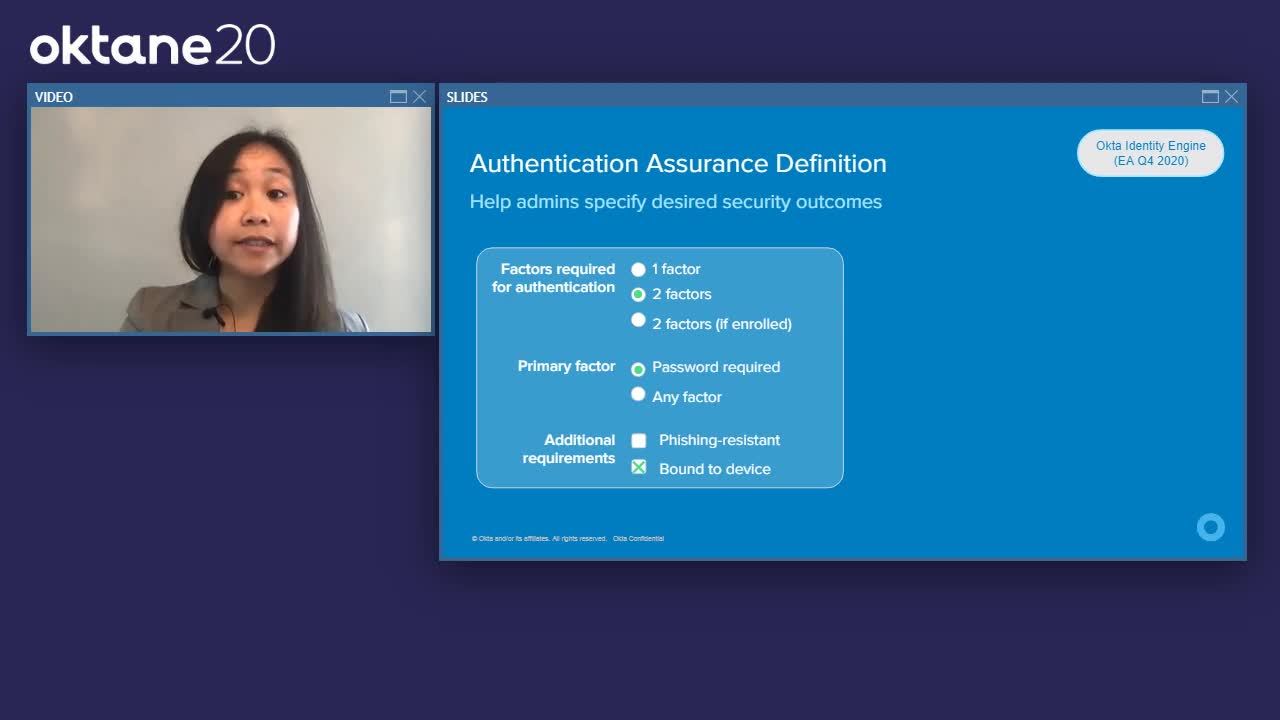
Thanh-Ha Nguyen: While, factor chains were very configurable and allowed you to achieve most of your desired security outcomes we saw that we had a lot of room for improvement. For example, admins had to define every chain which can lead to complex configurations as you can see on your right. Every new factor you add to your org would be a new chain. Additionally, when we moved to the world of per app authentication policies that we just described, we saw that it could get a little bit tricky to combine chain across apps. That's why with this feedback in mind this year, we plan to evolve factor sequencing into assurance definitions. Like today you will still be able to define the factors allowed in your org and the factors the users are allowed to use.
Thanh-Ha Nguyen: However, instead of defining all your own sequences, you define those Sharon's requirements that allow you to achieve your desired security outcomes. For example, one factor, two factors required, or two factors only if the user has an extra enrolled factor, password required or any factor allowed, and then specify additional requirements such as requiring phishing resistance through a factor like WebAuthn or requiring device bound factors such as Okta verify or any other TOTP enabled authenticator.
Thanh-Ha Nguyen: When a user is challenged for authentication, Okta will figure out which factors will allow them to meet that assurance definition. Just like its predecessor factor sequencing admins will still be able to define requirements based on login contexts. And as we discussed earlier, you can define specific assurances for different apps. Admins can still allow passwordless authentication. And these assurance definitions matched to multiple factors in the org. So users can use any factor that they have enrolled that matches that assurance, as more factors are added to the org. Okta will continue to evaluate whether that new factor meets the required assurance and only prompt the user for those factors if it meets those requirements. In short, we're building out assurance definitions to allow admins, to enable flexible factor combinations while also helping you achieve your desired security outcomes.
Thanh-Ha Nguyen: I've covered a lot of new features just now, but let's quickly put it all together. Say you're the CIO of a large org. You have hundreds or even thousands of apps and your team is adding a new app every month. Today, the team is managing each app policy separately. In addition to apps, your org might have many different types of users. For example, full time employees, contractors, and partners, each type of user has their own authentication requirements.
Thanh-Ha Nguyen: With Okta identity features we just talked about you can really simplify your policy management. Identity engine allows you to categorize apps into different levels of sensitivity, say not sensitive, highly sensitive or apps for contractor access and create one policy for each category. You can lower friction for your end users using tools like FastPass or Passwordless login with assurance definitions. For high sensitivity apps, you can set the assurance definition to require strong phishing resistant factors.
Thanh-Ha Nguyen: Adding a new app is as simple as it as linking the app to the correct policy and audits are also greatly simplified because you can just demonstrate one policy and show how it's linked to all the appropriate apps.
Thanh-Ha Nguyen: Finally, for your external users, say through a partner portal application, you can use those same assurance definitions that were used to simplify login for your employees for your end users. In this case, in your partner portal you can use assurance definitions to require multifactor authentication only if your partner, the user has enrolled in an extra factor. This is all defined through policy no extra coding required. With that I'll pass it back to Tomar.
Tomar Mayara: Thank you Thanh-Ha. Right. Now, let's see how Okta help you protect against threats. We are going to cover three big challenges. First, unfortunately, credential based attacks are still a serious problem. This is mostly due to low MFA adoption or inability to cover all your users in your org.
Tomar Mayara: Second, even when users enrolled in MFA, sometimes they aren't paying enough attention, clicking the wrong link or accepting the wrong push notification might lead to a compromised account even with MFA.
Tomar Mayara: Third, you don't always control the end user machine compromised devices can lead to compromised factors which can lead to compromised sessions.
Tomar Mayara: So what can be done about that? First, let's talk about our work that helps you drive MFA option. Okta is planning to release device identity SDK, which can be embedded into your mobile app and turn it into effect or the SDK eliminates one of the main option blockers. They need to download a dedicated app. Next FIDO2/WebAuthN is one of the most secure factors. Last year we witnessed the industry slowly removing two of the major blockers to adoption. Process support is significantly improved. Virtually all mainstream process, already support FIDO2. In addition to that, we see more and more devices embedding FIDO2 inside the hardware eliminating the need to acquire a separate hardware device. Okta [inaudible 00:18:32] FIDO2, of course. In the upcoming year FIDO2 is going to be part of assurance definitions, helping admins to leverage more aspects of the FIDO2 protocol. By the way, if you ever consider FIDO2 yet that's a perfect time to think about deploying it into your org.
Tomar Mayara: Users blindly accepting push notifications is a real problem. It is basically opening the door for credential based attacks. To help mitigate that risk based authentication and Okta Verify now work together. Here iss how it works. When Okta detects a high risk log in, we prompt the user to review the log in. Okta Verify would show three different numbers within the app. The desktop browser shows one of these numbers. The user then need to choose it within the Okta Verify app. This reduces chance of user accepting push notification they haven't initiated. These push notifications might in some cases be initiated by malicious factors.
Tomar Mayara: Last year, we released Threat Insight that gave us a glimpse into the world of large scale automated attacks. We are having great initial success with threatening sites, but we are only scratching the surface. So what's next? We are moving behind IP addresses, but it looks like [inaudible 00:20:00] are leveraging many different IP addresses. Some of them are mobile or even shared IPs. It is clear that we need to develop ways to mitigate these attacks and we need to do it without heavily relying on IPS. This progress will allow threatening sites to detect more advanced factors without increasing false positive rate.
Tomar Mayara: Another interesting aspect is what we call the unofficial client problem. We see all kind of third party clients, mostly email clients, which are probably not part of the official address for you. These clients often store sensitive information and [inaudible 00:20:39] this means that in case they're compromised, it might be a problem. In addition, users sometimes forget to update their password cause in repeat retries and potentially account up.
Tomar Mayara: As we mentioned this before, Okta Risk Score is going GA in May. The next step for us is to open our risk engine to partners and customers. We are planning to make it easy for external systems to digest our Risk Score. We are also building API is for partners to inform the risk engine. The risk ecosystem allows customers and partners to use Okta as policy and enforcement clarity, meaning denying access for specific users, stepping up or terminating Okta session. All that based on both Okta risks and external events.
Tomar Mayara: All right, so we've covered enough ground here. Let's do a quick recap. We showed the Okta MFA adoption. We discussed the device identity as decay, which is turning your app into FIDO. We also covered the industry by the adoption of FIDO2. Then we talked about risk space of indication for Okta verify. We showed how it reduces the chance of a user accepting malicious push. On threat detection fronts, we talked about the unofficial client challenge and how bad factors IP addresses. Also, we are opening risk engine for our partners and customers ecosystem. Thanah-Ha back to you.
Thanh-Ha Nguyen: Finally, in 2020, we are making a lot of investments in building new tools to increase end user self service and help you lower help desk costs. In the past most of the burden of reviewing logins and unusual security events has fallen on the Okta admin and security teams, parsing logs from Okta system log. Outside of security notifications the end user had very little visibility into their own account activities. This year, we're expanding the end user visibility tools by adding end user recent signins and security events to the dashboard. These features allow end users to view their previous logins sorted by device view, recent account changes and if they don't recognize an activity, they can report the activity to an admin directly from the dashboard.
Thanh-Ha Nguyen: For any developers building apps on top of Oktas APIs, we will be building these features directly on new public APIs. So any application can add their own activity log features. To set the foundation for a new end user security features like recent sign-ins we're actually redesigning the entire end user account settings experience. We've heard from customers that Okta is already played a huge part in helping end users, self service, manage their profile and factors today. However, we still have a lot of opportunities in the space where if we can take even more burden off the help desk.
Thanh-Ha Nguyen: Like our new and user's dashboard, the end user settings page is designed with accessibility and responsiveness in mind so that end users can manage their settings from any device that they're accessing Okta from. This design gives us the foundation to embed account management features into any Okta experience from the end user dashboard to admin apps, to even the Okta verify mobile applications. Beyond this VR visual redesign, we're also building account management capabilities on all new public APIs with end user scopes. So that again, any developer building apps on top of Okta can build their own customized account management experiences for their applications as well.
Thanh-Ha Nguyen: Last but not least this year, we're also revamping our factor management experience, specifically factor recovery experiences. We've heard from many customers that today factor management can be a difficult experience for end users. If a user loses their phone, which had Okta verify or lost their YubiKey, they were required to go to the help desk to get their factor reset, or re-enrolled. This year we're rethinking this factor management experience by providing flexible account recovery. We're expanding factor management so that you can recover a factor using any other factor per admin defined policy. This means that admins can set policies so that users can recover their lost Okta Verify with password and WebAuthn, for example. We're expanding the capabilities of self service password recovery so that you can recover password with any factor. Yes, this does mean that you can remove security questions from your org and recover with Okta verify and email instead.
Thanh-Ha Nguyen: Finally, to reflect the reality that users own and access Okta from multiple devices, we're expanding our Okta verify support to support enrollment, a multiple instances so that you can have Okta Verify on your Apple watch, on your phone, anything. With that context, let's see a quick demo of how SSPR self service password reset could work in this new world.
Thanh-Ha Nguyen: Let's put ourselves in the shoes of Pam, the paper company that she works at makes her change her password all the time. So she can never remember what she set it to less previously. She had to reset her password with email and security question. Today, Pam got an email saying that she can use WebAuthn with touch ID to reset her password instead. Let's see how this looks. So here we see Pam logging in with her username and she's prompted to log in with her password, which she's already forgotten. So here she can click on forgot password. And she sees that now, in addition to email, she has an option to recover her password with Mac book touch ID, by clicking on Mac book touch ID she sees that her Chrome browser is prompting her for login with a fingerprint. And she's immediately taken to a page after verifying her fingerprint to set a new password after setting it and confirming it she's immediately redirected to where she wanted to login in the first place, her new end user dashboard.
Thanh-Ha Nguyen: After this really quick process of recovering her password. Pam realizes that this is a much easier way of recovering her password. And she did know that her security question wasn't very secure anyways. Everyone in the office knew she got married in Niagara falls.
Thanh-Ha Nguyen: All right, so we've covered a lot of features in the last 30 minutes and we've gone really deep into how these features could work, but let's take a second to zoom out and take a look at the whole forest, not just the individual trees. This year we covered a lot of features about how we can help admins address real challenges. We're building features to simplify policy management. We're providing more threat intelligence tools and building out new features for end user self service. However, that's not it, if you were at Oktane19 or have been following Okta over the last year, you've probably heard us talk a lot about zero trust, including where Okta fits into leading frameworks from Forrester, Gardner, NIST and others.
Thanh-Ha Nguyen: Just to level set for those of you newer to this conversation. When we talk about zero trust, what we mean here is the necessary shift that insecurity that goes along with increased cloud and mobile adoption. Traditional perimeter oriented approaches based on networking security don't really make any sense anymore. Our users are accessing more resources from more places and more devices than ever before. Here at Okta we're investing in products that help you, our customers be grounded in identity and access management. Namely, making sure that the right people have the right level of access to the right resources in the right context, acts assessing this continuously with the least friction possible.
Thanh-Ha Nguyen: Let's start with the right people. We've talked a lot in this presentation, our continuing investment in strong authenticators from WebAuthn to Okta verify experiences, both in our app and our new SDK. We believe that strong, authenticators will be key to ensuring that the users accessing your resources or who they say they are. With our investments in Okta identity engine with authentication assurance definition and per app policies, we make it easier for the users to have the right level of access. Okta identity engine allows you to match the authentication requirements to the sensitivity of the resources. A user is accessing.
Thanh-Ha Nguyen: Speaking of resources while Tomar and I have used SAS apps as examples in most of the sessions so far, Oktas access policies apply to a wide variety of resources. For example, with products like Okta access gateway, API access management, and advanced server access. Okta lets you protect legacy, apps, API and infrastructure, respectively. To learn more about these products. We highly recommend you attend their respective sessions,
Thanh-Ha Nguyen: In Okta zero trust philosophy, it's not just the user identity that we need to know. We need to evaluate context as well. In this session, we've touched only briefly in our investments in devices as a first class citizen in Okta to learn more, we highly recommend you attend the devices roadmap session as well.
Thanh-Ha Nguyen: Our North star here on the security products team is to help you achieve continuous authentication. We're making great strides with per app policies via Okta identity engine. However true continuous authentication is a longterm project involving not just Okta, but the ecosystem of apps and resources our users access. Our chief product architect, Carl has an entire session dedicated to this that you should go check out.
Thanh-Ha Nguyen: Last, but definitely not least we want to make sure that not only that you our admins are successful, but your end users are as well. We know that they want to access everything as seamlessly and frictionlessly as possible. This year, we're building out FastPass, continuing our investment in WebAuthn and improving our risk based authentication experiences. All of these products are aimed towards helping you protect your orgs while minimizing end user friction. We know that the path to zero trust and continuous authentication is a journey and everyone is starting at a different place. Our goal here at Okta is to build tools, to make easy for you, to move towards all our common shared goal with that. Thank you for your time and listening. I talked about some recommended sessions, but here's a few quick blurbs about them right here.
Security is crucial for every organization. In this session we will cover Okta's security roadmap and vision on how companies can adopt Zero Trust principles to secure their customers and the extended enterprise.
