- Home
- Single Sign-On
- Citrix Gateway
Overview
This app integration supports Single Sign-On. See Capabilities for more details.
The Challenge
With the explosion of cloud apps and SaaS, the center of gravity of identity management is increasingly moving to the cloud as well. At the same time, end-users still require easy access to legacy enterprise apps via tools like XenApp and XenDesktop to enable and support their mobile workstyle. A complete IDaaS solution is needed that can integrate and unify these two worlds to improve administration and boost end-user production.
The Solution
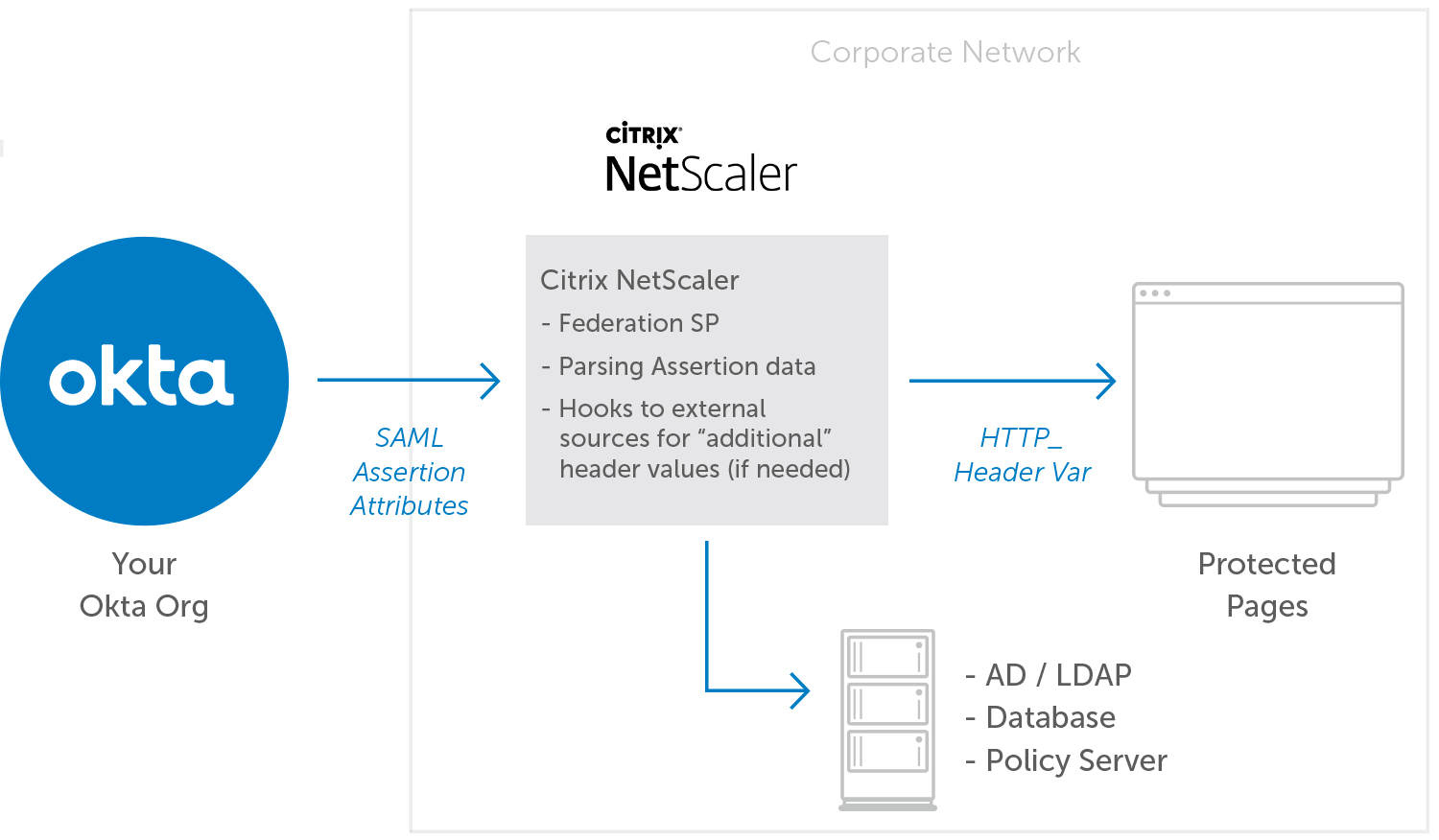
Once Citrix NetScaler is deployed and configured with Okta, IT admins can manage access to cloud and legacy enterprise apps through a single pane of glass in the Okta admin console. IT admins are able to strengthen the security of all applications through centrally managed security policies that can be used by both cloud apps and NetScaler-fronted enterprise apps.
With NetScaler integrated to Okta, end-users can authenticate once into Okta and seamlessly access both Citrix apps and on-prem apps (like Sharepoint). In addition, NetScaler extends Okta’s authentication capability to applications outside of the Citrix portfolio that do not have native authentication mechanisms or support header-based authentication.
Application Authentication Mechanism |
Integration |
|---|---|
|
Pre-built Integration in Okta Application Network (5000+ integrations) |
Okta |
|
Federation protocols SAML, WS-Fed, OpenID Connect |
Okta |
|
Any Application with a Login Form |
Okta |
|
Citrix apps (e.g. XenApp & XenDesktop) |
Okta + NetScaler |
|
No Native Authentication |
Okta + NetScaler |
|
Kerberos/NTLM Exchange Authentication |
Okta + NetScaler |
|
Header-based Authentication |
Okta + NetScaler |
|
Reverse proxy—Access on-prem app from outside firewall |
Okta + NetScaler |
|
Secure HTTP traffic to/from on-prem app |
Okta + NetScaler |
Enable B2B access to Citrix and on-prem apps
It can be a challenge to expose virtual apps via XenApp/XenDesktop and on-prem apps like Sharepoint Server to external users such as partners and contractors. A traditional solution to this problem would be to integrate with each individual external Active Directory or LDAP server.
NetScaler supports federation for Citrix apps natively and for enterprise web apps using SAML to Kerberos Constrained Delegation. Okta, paired with NetScaler Unified Gateway, can manage contractor or partner identities and enforce multi-factor authentication.
Single end-user portal for all apps, on-prem and cloud
The Okta portal makes it easy for end-users to access all their apps from a single location. Typically, organizations using the Okta portal want all the end-users’ applications exposed and accessible through the portal. Integrating Okta with NetScaler enables the user to log in once to Okta, and access cloud applications like Salesforce, G Suite, and Box, as well as Citrix apps like XenApp/XenDesktop, in one place.

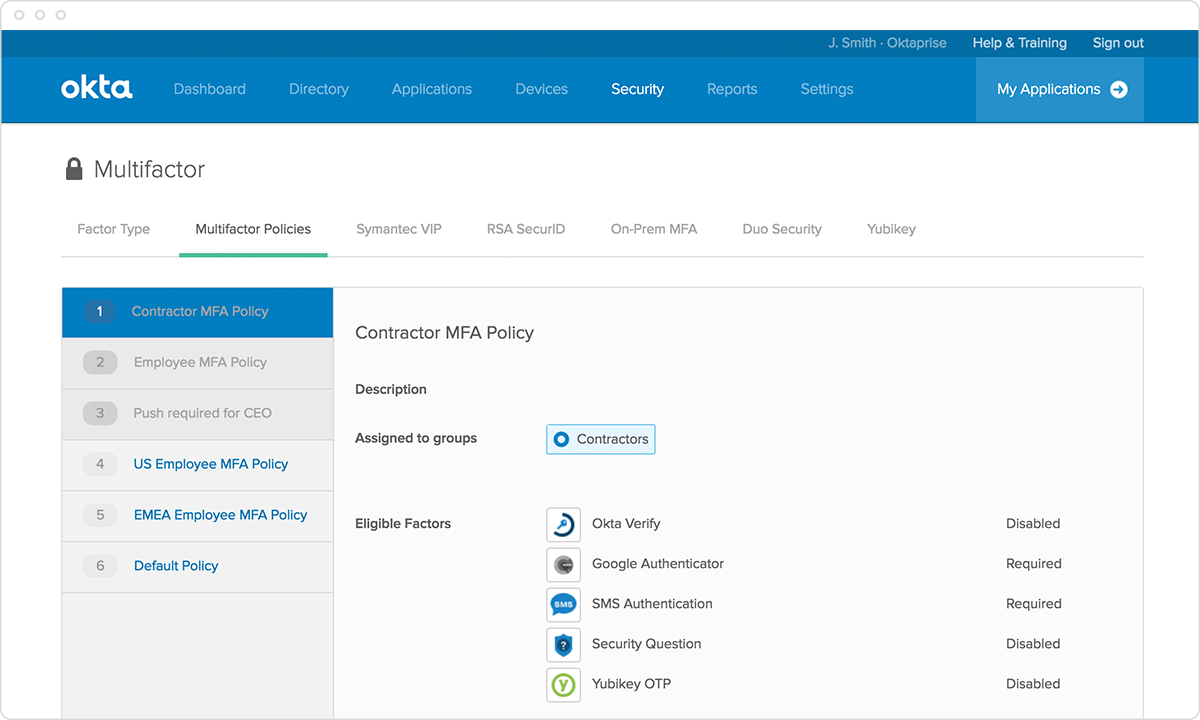
Increased on-prem security with MFA
Enterprises are moving to IaaS to allow services to be more easily reached from any network. But in moving to IaaS, enterprises need to have a strategy for protecting access to those resources. Given the greater exposure, it is a best practice to require multi-factor authentication to access these services. Okta can easily add multi-factor authentication with a soft token (iOS, Android or Windows Phone), SMS or voice as factors.
Functionality
Add this integration to enable authentication and provisioning capabilities.
Authentication (SSO)
-
API
-
Cross App Access
-
Entitlement Management
-
Event Hooks
-
Identity Security Posture Management Identity Security Posture Management helps to harden the identity attack surface proactively, by identifying vulnerabilities, prioritizing risks, and streamlining remediation.
-
Inbound Federation
-
Inline Hooks
-
Outbound Federation
-
Partial Universal Logout
-
Privileged Access Management
-
RADIUS
-
Secure Identity Integrations - Advanced Supports 4 of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Secure Identity Integrations - Fundamental Supports 3 of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Secure Identity Integrations - Strategic Supports 5+ of the following integration types for the 65+ business-critical applications: SSO, SCIM, entitlements, universal logout, workflows, and ISPM
-
Universal Logout
-
Workflow Templates
-
Workflows Connectors
-
SAML Security Assertion Markup Language is an open standard for exchanging authentication and authorization data between an identity provider (IdP) and a service provider (SP) that does not require credentials to be passed to the service provider.
-
SWA Secure Web Authentication is a Single Sign On (SSO) system developed by Okta to provide SSO for apps that don't support proprietary federated sign-on methods, SAML or OIDC.
-
WS-Federation
-
OIDC OpenID Connect is an extension to the OAuth standard that provides for exchanging Authentication data between an identity provider (IdP) and a service provider (SP) and does not require credentials to be passed from the Identity Provider to the application.
Provisioning
-
Create Creates or links a user in the application when assigning the app to a user in Okta.
-
Update Okta updates a user's attributes in the app when the app is assigned. Future attribute changes made to the Okta user profile will automatically overwrite the corresponding attribute value in the app.
-
Attribute Sourcing The application can be defined as the source of truth for a full user profile or as the source of truth for specific attributes on a user profile.
-
Deactivate Deactivates a user's account in the app when it is unassigned in Okta or their Okta account is deactivated. Accounts can be reactivated if the app is reassigned to a user in Okta.
-
Sync Password Push either the users Okta password or a randomly generated password to the app. This feature is not required for all federated applications as user authentication takes place in Okta, however some apps still require a password.
-
Group Push Push existing Okta groups and their memberships to the application. Groups can then be managed in Okta and changes are reflected in the application.
-
Group Linking Link Okta groups to existing groups in the application. Simplifies onboarding an app for Okta provisioning where the app already has groups configured.
-
Schema Discovery Import the user attribute schema from the application and reflect it in the Okta app user profile. Allows Okta to use custom attributes you have configured in the application that were not included in the basic app schema.
-
Attribute Writeback When the application is used as a profile master it is possible to define specific attributes to be sourced from another location and written back to the app. For example the user profile may come from Active Directory with phone number sourced from another app and written back to Active Directory.
Documentation
Here is a section all about documentation, integration, and implementation.
-
Blog post:
Okta + Citrix Integration: Complete Access to Citrix, Cloud, and On-prem Apps
Read it -
Datasheet:
Okta and NetScaler for Complete Access Management for Hybrid IT
Read it -
Datasheet:
Okta + Citrix NetScaler for Healthcare: Secure and Simple Access to Patient Data from Any Location
Read it -
Configuration Guide:
Citrix NetScaler Gateway SAML
Read it -
Configuration Guide:
Citrix NetScaler Gateway RADIUS
Read it