Advisory 2020-008: Mitigating the Risks of Copy-Paste Compromises
Australian Prime Minister Scott Morrison recently raised awareness of a state-based cyber attack that Australia is facing across all levels of government and the private sector. In response, the Australian Cyber Security Centre (ACSC) published an advisory on the nature of the attacks as well as guidance on how to mitigate these types of attacks in the future. The advisory, titled “Copy-paste compromises - tactics, techniques and procedures used to target multiple Australian networks,” is specific to the threat actor’s use of proof-of-concept exploit code, web shells, and other tools copied identically from open source resources.
In this post, we provide a summary of the attack, a recap of the guidance given by the ACSC for mitigation, and how Okta’s multi-factor authentication (MFA) product can help.
Attack overview
The Australian Government is currently aware of and responding to a sustained targeting of both independent and government organisations carried out by a sophisticated state-based actor.
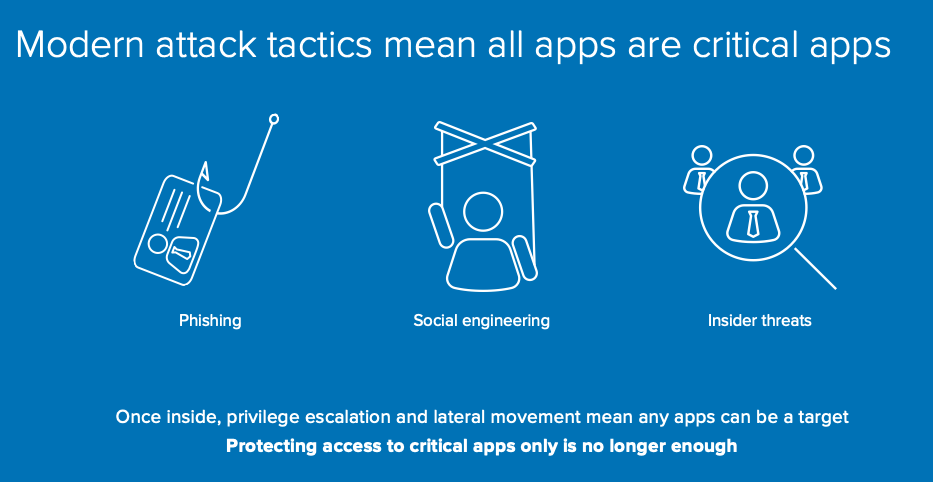
The advisory reported that the attacker has been prevalent in targeting and exploiting public-facing infrastructure as well as vulnerabilities over unpatched versions of Telerik UI, the deserialisation vulnerability in Microsoft Internet Information Services (IIS), a 2019 SharePoint vulnerability, and the 2019 Citrix vulnerability.
In this attack, the threat actor could quickly leverage public exploit proofs-of-concept to target networks of interest. The threat actor also continuously surveyed target networks, looking for vulnerable services—most likely maintaining a list of services to target. Additionally, the threat actor could identify resources under development and/or orphaned services that were not well maintained by victim organisations.
When the exploitation of public-facing infrastructure did not succeed, the ACSC identified that the actor utilised various spear-phishing techniques, including:
- Links to credential harvesting websites
- Emails with links or attachments to malicious files
- Links prompting users to grant Office 365 OAuth tokens to the actor
- Use of email tracking services to identify the email opening and lure click-through events
ACSC recommended prioritised mitigations
As a result of these attacks, the Australian Cyber Security Centre has identified two key mitigations which would have greatly reduced the risk of compromise:
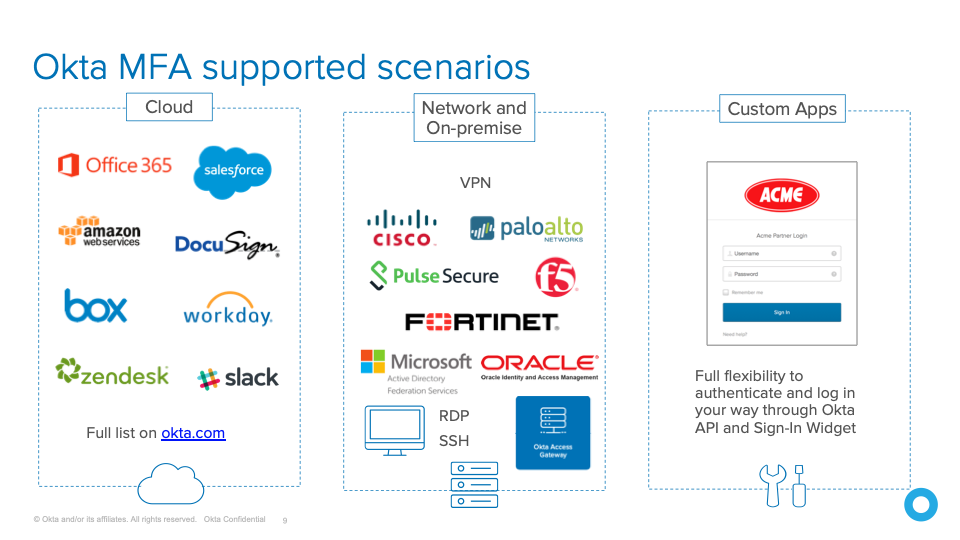
Use of MFA across all remote access services
Multi-factor authentication should be applied to all internet-accessible remote access services, including:
- Web and cloud-based email
- Collaboration platforms
- Virtual private network connections, and
- Remote desktop services
Prompt patching of internet-facing software, operating systems, and devices
All exploits utilised by the actor in this campaign were publicly known and had patches or mitigations available. Organisations should ensure that security patches or mitigations are applied to internet-facing infrastructure within 48 hours. Organisations should also use the latest versions of software and operating systems whenever possible.
How Okta accelerates the ACSC recommended prioritised mitigations
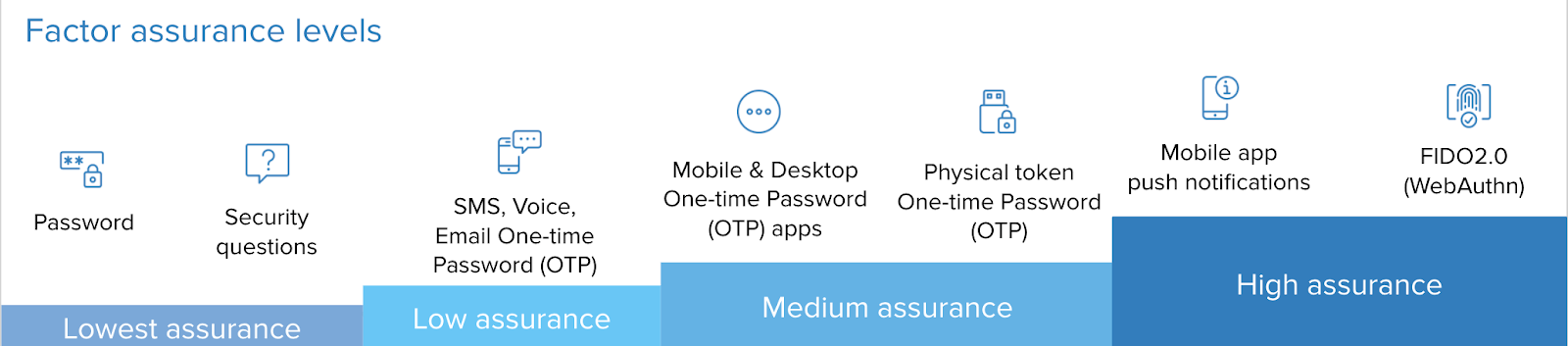
With Okta’s Adaptive MFA, any organisation can enforce strong authentication by allowing users to be verified with something they have rather than something they know. Okta integrates with a wide and robust set of two-factor authentication options providing flexibility and choice to every organisation. Security teams can provide the correct level of assurance mandated by their security policies, governance, industry regulations, and compliance requirements whilst also considering usability and optimal end user experience as part of the decision process.
Additionally, organisations can combine the access decision with risk level for a login. For example, high-risk logins could require a strong authentication factor like FIDO2.0, while low-medium risk logins could be paired with a lower assurance factor.
With Adaptive MFA, Okta helps customers protect their most critical systems, including all of the services mentioned by ACSC above. Okta can be the single authentication provider for all services for your organisation, or it can be integrated with an existing authentication provider to provide or enhance MFA capabilities.
ACSC recommended additional mitigations
Beyond the ACSC recommended key mitigations above, the ACSC strongly encourages organisations to implement the remainder of the ASD Essential Eight Controls.
During the incident review, a common issue that reduced the effectiveness and speed of investigative efforts was the lack of comprehensive and historical logging information across a number of areas including web server request logs, Windows event logs, and internet proxy logs. The ACSC strongly recommends reviewing and implementing its guidance on Windows Event Logging and Forwarding and System Monitoring.
How Okta addresses the ACSC recommended additional mitigations
Effective incident detection is built on the capability to identify security incidents with minimal dwell time.
Security operations are looking to answer:
- “Who accessed my applications?”
- “On which network?”
- “On which device?”
- “How long have they been accessing my systems?”
- “Which data has been targeted?”
- And most importantly, “What evidence did they leave along the way?”
Security teams can combine the data from Okta with logs from other security tools and applications for incident enrichment to piece together the entire incident picture and identify the key indicators of a compromise. The partnerships Okta has built with different security providers help us deliver a world class end-to-end Zero Trust architecture solution which allows organisations to deliver a Security Orchestration, Automation, and Response capability. Organisations can integrate Okta with tools like Proofpoint for email and advanced threat protection, Netskope for secure applications, VMWare Workspace One for mobile device management, and Splunk or Sumologic for complete visibility and analytics across all systems.
ACSC recommended detection advice
“This advisory does not attempt to include detection technique recommendations for all attack techniques identified. For general detection and mitigation advice, please consult the ‘Mitigations’, ‘Data Sources’ and ‘Detection’ sections on each MITRE ATT&CK technique web page.”
The ACSC strongly recommends that organisations review and implement the identified tactics, techniques and procedures (TTPs), detection recommendations, and indicators in this advisory and associated files to help identify malicious activity related to this campaign.
How Okta enables the ACSC recommended detection advice
In the security world, data visibility and availability will allow you and your organisation to make smarter and better decisions. Okta Adaptive MFA leverages context from multiple sources to decide if the incoming request is valid or malicious. Context can be in the form of users, applications, network, devices, and even the data itself. Okta takes advantage of all these available data points within its adaptive policy framework to determine in real time whether it is a legitimate action or not.
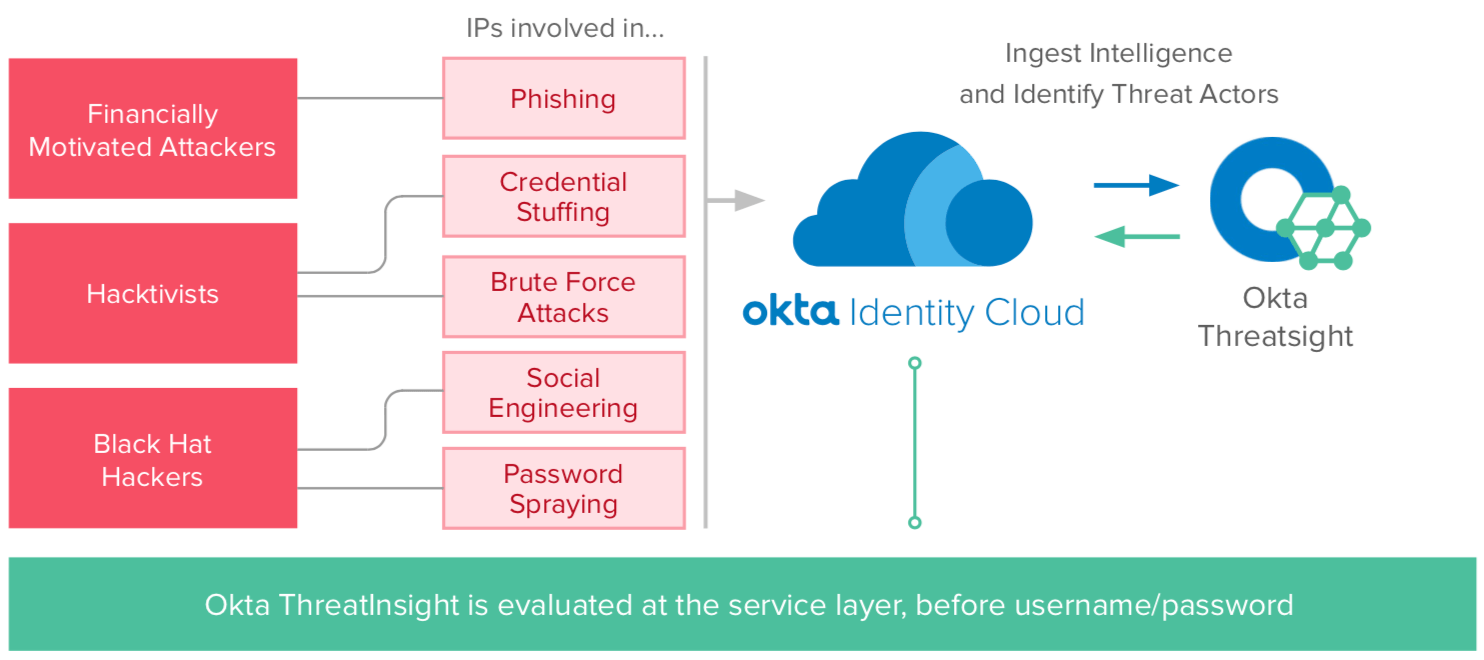
Across our thousands of customers, billions of authentication events transpire within Okta every hour of every day. Using machine learning techniques across this vast dataset, Okta can deliver a proactive risk-based authentication capability, which allows early detection of suspicious activity and preemptive blocking of malicious attempts.
As more customers around the world subscribe to the Okta Identity Cloud, the network effects of this service continue to grow, making organisations even less susceptible to attacks as time goes on.
In summary
In line with the announcements made by the Australian Prime Minister over the recent security attacks spanning different industries, the Australian Cyber Security Centre mandates that all organisations adopt a multi-factor authentication strategy and deployment over the different technology stacks they are using.
Implementing an MFA strategy requires careful handling and balance as users can be greatly impacted as part of this roll-out. As such, organisations need to consider an MFA strategy that will give them the flexibility to choose a wide range of options that can cater to different levels of security assurance whilst maintaining balance with user experience and ease of deployment.
Lastly, the success of any organisation’s security strategy relies on proper security awareness. The weakest link for any security strategy is the end-user themselves; without proper security awareness training and communications, many users will continue to be susceptible to malicious attacks.
To learn more about how to use MFA to protect your organisation, check out the below resources:


