Oktane19: Customer Spotlight: How We Reached 100,000 MFA Registrations in 100 Days
Transcript
Details
Jade: Okay so thank you so much for coming to our session with Monash University on how they have reached a 100,000 registrations in just a 100 days. So, safe harbor slide, there was some road map we discussed soon. So, this is, typical legal documentation. So my name is Jade, and I'm the product manager for End User experience at Okta. And, what we really thrills me about having Monash here with us today, partly as an Australian, is that Monash is constantly the top, top one percent of universities around the world.
Jade: They're the largest university in Australia and leaders in research that says biometric, IBF, and the world mosquito program. And they're user base is, spans across the world with campuses across Asia, India, and Africa. So given that, they're IAM story with Okta has been really incredible with a loves BN scale. Including a 170000 users in Okta. A 130000 users in MFA. 60000 groups and over 250 applications. And having had done this is just a hundred days we're really really proud to have them here to share their story with us. So without much further ado, I like to introduce Cameron and Andrew to come on stage.
Andrew Collins: Hello everyone. My name's Andrew Collins, I'm a solution architect for the identity team at Monash university.
Cameron Duck: And I'm Cameron Duck, I'm the lead systems engineer for single sign for the identity team as Monash uni.
Andrew Collins: So I don't need to tell you why MFA is so important for your organization. One of those reasons for us was the silent librarian. So this is a fishing attack that's targeting universities with research data. So far they've taken 31 terabytes of data costing universities around the world three point four billion dollars. So back in, 2017 we started to role out MFA with our existing ADFS environment.
Andrew Collins: So at the time, the user experience was really really poor and some of the core requirements that we needed just didn't exist with ADFS. So we needed to go to market and find another product. And this is where we found Okta. So along our journey with Okta we discovered we could do a lot more then just MFA. We could then migrate all of our applications from ADFS over to Okta. We could also then look at using skin provisioning for some of our applications like work place and slack. And also implement API management so then we could integrate MuleSoft and help strengthen our APIs.
Andrew Collins: Now one of the core things with Okta was the user experience. Signing in, signing out for MFA was really easy for the user, it was just really following a bouncing ball. One of the other core requirements was to be able to remember the user's device as well. As Okta is a cloud provider we were able then to remove our ADFS infrastructure. So then we didn't need to worry about patching systems or upgrading them and looking at performance.
Andrew Collins: So how did we roll this out to organization our size? So we need to break this down into three manageable phases. Our first phase was to feel around Okta with ADFS. And our second phase was then to migrate all of our applications from ADFS over to Okta. And our last phase was to role out MFA to our organization and this was going to be one of our biggest challenges.
Cameron Duck: Right O, so this is how we set off users with log in cards, ADFS, pride themselves, they get a SAML assertion for which of the various applications that they wanted to access. The first thing we had to do in our migration was build up our Okta org and federate it. Join it with ADFS. We needed to make sure Okta would pass through all the attributes, that ADFS would need to create any assertion for any application, and we needed to make sure that ADFS would take those new attributes rather then the ones coming directly from AD. Then came cut over day.
Cameron Duck: So, across about five hours we changed the home room or the login page for each of our applications in ADFS so that it would then present the Okta login page so that users went from seeing only the ADFS login page to only seeing the Okta login page even though the AX was still connected to ADFS. This was the biggest change that our user base was gonna see and we did it across one day.
Andrew Collins: So once we finished our first phase, we could move onto the second phase by moving all the applications from ADFS over to Okta. So what we really needed to do early on in the project was get the contact details of the applications as early as possible. So this a very time consuming task, once we got this information we could send out what the user needed to do and when. We also then created a schedule. So, a migration schedule which consisted of 20 windows over the 34 day period. So then application is selected one of these windows on when they were going to migrate.
Andrew Collins: So we kept this at about ten applications in these windows so then we could concentrate just on migrating those ones in that window. So how did we help our application owners migrate? So we were able to pre-stage all of our applications in Okta prior to the migration windows. This allowed us then to send the meta data and configuration files to the user so then they could work out what they needed to change. We also provided it into a QA environment so then they could also run their full end to end tests.
Andrew Collins: This also made them feel very comfortable on the migration day. So one of the things we needed to make sure is our Okta admins were well trained in Okta but more importantly trained in trouble shooting SAML. So, we have a lot of applications that the owners aren't technical people. So we needed to jump in there and help configure their app or trouble shoot some SAML, see if they're getting their assertions.
Andrew Collins: So if we didn't do this we wouldn't have been able to migrate their apps at this speed. So after we migrated our apps we were able to enter, start rolling MFA. So one of the things, one of the key things for this was to get your sponsors on board, so make sure your executive team want this rolled out. So this is really easy for us to do because of all the breaches recently in the news. The exec team wanted this rolled out yesterday.
Andrew Collins: So we cashed in on this idea and decided to use our executive team and our IT department as our pilot users. So early on in the piece, we found that was really no graceful way of introducing MFA out to our organization. So we came up with this idea to create an opt in page. So what this is a page where a user could go to and opt in for MFA at a time convenient to them. So just imagine rolling MFA to thousands of ten thousand people at a time. And, they might have had a presentation to do or, student had to submit an assignment.
Andrew Collins: So this is one of our core things of rolling out MFA. As for the actual rollout process we advertise this page for around bout two weeks and then we enforce them to use MFA after that two week period. And we roll this out in stages through our faculties and then batches of students. So while we're rolling this out we make sure all our support mechanisms were in place as well. So we had people walking around helping people sign up for MFA. We also had our service desk, when someone was calling they'd also help sign up for MFA.
Andrew Collins: One thing that we needed to get right from day one as well was our instruction page and our FAQ pages. So these were very detailed, we had instructional videos on how to sign up for MFA and then how to change your device. Our FAQ pages were in different categories so it was really easy to find your answers. And these lead to sections like general use, what if I've lost or my phone's been stolen or I got a new phone. Traveling to a new country. And we had sections on privacy as well.
Andrew Collins: So it's really important that this page is a public link and not behind authentication, cause if they're having difficulty logging in then they would be able to get to the help pages.
Cameron Duck: Righty O, as you can imagine, the factors that you choose are very important. You want to make sure that you choose factors that are secure enough so it's not easy to get in through your brand new security you just built but also user friendly enough that you don't have a backlash from your user base. Or in some cases have them try and circumvent your multifactor authentication. So the factors that we went with were Okta verify with Push, Google authenticator, UBKOTP. And U2F. Went with Okta verify because it's very easy to sign up, just scan the QR code, of you go.
Cameron Duck: And then when you go to use it, you get a notification on your phone, you check that that yes that is you that's trying to login and click approve. Google authenticator was turned because we have some user base that doesn't change over their phones very often, can have very old operating systems. Some so old that Okta verify wouldn't actually run on it. And because there's so many different authenticator apps we were able to find, most of the time find one that would work on those phones.
Cameron Duck: We also used it as a back up code, cause currently Okta verify doesn't restore when you change phones over with some authenticator app to. The U2F factor is another very easy to use factor, you plug your key into the side of your laptop, you press the button and you're in. Once again we ran into a couple of problems, our VPN doesn't support U2F and neither did some browsers. So for users that didn't have a phone we provided them with a Ubikey and used the one time password factor.
Cameron Duck: Now you notice that we didn't go with security questions or SMS voice. That's because the security questions are very easy to get around, to socially engineer the answers. And for SMS voices it's also easy for the person trying to get into your account, they can call your phone company and convince them to port your number to their sim win which case they will get the SMS message to give them the code to log into your account.
Cameron Duck: I will now walk you through the process we set up for our users so they can opt in for MFA. They visit our opt in website, MFAoptin.monash.Edu. They are given some information about MFA and why the university's rolling it out. They then click next. Here they can select the type of smart phone they have, enter their mobile number and click send me a link. This will send an SMS to their phone which contains a link to Okta verify for their operating systems app store. If they do not have a smart phone or are not able to install the app there's a link with other options for them.
Cameron Duck: Once they installed Okta verify, they click on register now to continue the process. They will need to login with user name and password. This brings the user to the MFA enrollment process. All of our users by default have the Okta verify and Google authenticator factors available for them. The user then enrolls Okta verify. The user has the option for enrolling for another factor or finish the process by clicking finish. What the user does not see is that they're account is added to a group which is linked to our policy that says they must MFA every time from now on.
Cameron Duck: Right O, we had a couple of special scenarios that we had to consider. Our first are our customer roll accounts. These are accounts that multiple users use, for example reception for a building, things like that. So for these account we used Google authenticator because you can enroll multiple devices against the one account. We had some scenarios where the users that logged into the account, not only were they not in the same building, they weren't even in the same location or in extreme cases, the same country.
Cameron Duck: So having a single device that was kept at the desk wasn't any good for us. The next one were our senior staff that have executive assistance. Unfortunately some of our applications don't allow for delegated tasks, so for the EAs to do their job they need to log in as their boss. So in these cases the senior staff member would enroll Okta verify on their phone and then would set up a Ubikey and give that to the assistant so when they need to log in as their boss they could do that.
Cameron Duck: As a research university, we have a number of labs that people aren't permitted to bring their phones or Ubikeys in and they have, of due to contamination reasons, whether that's bringing contaminants out of the lab or bringing them in. So in those cases we set up a network zone that said any machines that are in these labs, they don't need to MFA. Doesn't matter who logs into them. The lock on the door for the lab, we consider the second factor. Our last scenario were our electronic exams or the assessments. So, Monash university is currently doing electronic exams so no longer the students need to bring a pen and paper and write their essays out and tick ABCD, all that sort of stuff.
Cameron Duck: They can do it on a laptop, in the room. But as you can imagine, examiners don't really like students bringing their own phones into an exam. So, we worked with our network team to be able to set up another network zone with it's own policy that we can turn on and off during exams. To say that any students logging into these laptops don't need to MFA. We are working later on this year to be able to do a big AOD for the exams and I'm sure that's gonna be another conversation with our network team to work out exactly what we're gonna need to do for those ones.
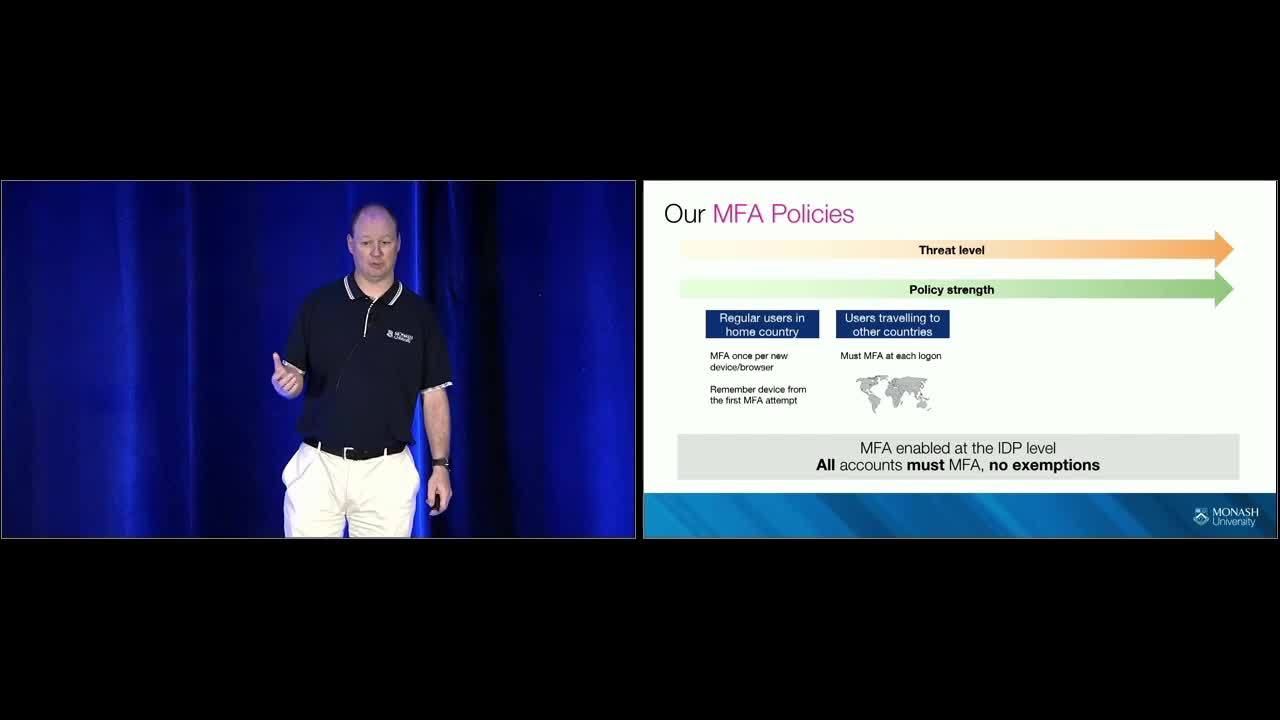
Cameron Duck: Now, Some of our signing policies, because the direction that we were given by our COI at the start of the project was that all accounts must MFA for all logins for all applications, all of our policies are set up at the top IDP level, there is no policy sign set up for individual applications, everyone must follow the same set of rules, no exemptions.
Cameron Duck: So if I'm a regular user, I come to work everyday, I'm a student, come on campus to study, or I'm studying from home. I, go to my email or something, username, password, go for the second factor, get the push to my phone, accept. There's a tick box that says don't prompt me on this device again and if they do that they never have to MFA again from their own laptop, it's just the one-off time. They also have a long session life so worst case scenario they have to login twice a day if they work 24 hours a day.
Cameron Duck: Our next scenario, as you saw, we have people all over the world and people traveling all over the world so we set a policy that says the first log in from a new country once again you must MFA. So when I landed here in San Francisco, grabbed my laptop, go to log in, check my email, even though it was my laptop, I ticked the box before, I still had to MFA because it's a new country and I'll have to MFA again when I'll get back to home to Australia. A VPN is set up for MFA now as well. Because the VPN's a good access point into our network, we made sure that you must VPN, you must MFA every time you VPN because we wanna make sure that the people on our network our meant to be our network.
Cameron Duck: And lastly our privilege users, we increase security for our privileged accounts, so for example all of our Okta admins, they're only allowed to use a U2F token as their second factor, no Okta verify, anything like that. Just U2f, have a very short session length time. We wanted to make sure that our accounts that have the most access also have the highest security on them.
Andrew Collins: So during our roll out of MFA we came up with a few different challenges. So the first ones were people that didn't have a mobile device, and also people who didn't have a supported device so they couldn't install the Okta verify app. And one of the most frustrating things was people who didn't want to use their personal device for MFA. So our solution was to this, to supply them a Ubikey.
Andrew Collins: So this worked in most cases except for when they wanted to access say email on their phone and it didn't support USB. One of our biggest challenges was the operational support. So, we concentrated on rolling out MFA as quickly as possible and protecting our organization and we're very happy at how this went. But the number of people who either lost their phones or damaged or upgraded their phone, we were getting around about a thousand of these per week. Now because we didn't select SMS, it wasn't as simple as taking SMS out of one phone and putting it the other one and they continue to do MFA. So they had to call the service desk.
Andrew Collins: So, at the moment we're working on a back up feature so what this is, it's a website that users can go to, register for 10 one time backup codes and store that safely in a personal vault or wherever. And when they need to reset their phone they can go back to the website and enter in their one time code and reset their own factor. So I'm about to show you a demo of what this looks like today.
Cameron Duck: I will now walk you through the process we set up for our users so they can opt in for MFA. They visit our opt in website, MFAoptin.monash.Edu. They are given some information about MFA and why the university's rolling it out. They then click next. Here they can select the type of smart phone they have, enter their mobile number and click send me a link. This will send an SMS to their phone which contains a link to Okta verify for their operating systems app store. If they do not have a smart phone or are not able to install-
Cameron Duck: The app there's a link with other options for them.
Cameron Duck: What's that?
Cameron Duck: Once they-
Andrew Collins: That was the wrong video.
Cameron Duck: That was clearly the wrong video.
Andrew Collins: Okay, I will just continue on. So just to recap, make sure you know who you're going to impact. Get your support early from your executive team, plan ahead. And make sure you have a really good rollout strategy. But most importantly, support your end users throughout your journey and beyond. So what's on for the year for us? Well, we need to release our new backup codes feature and I wish we could show you that. We're also looking at integrating Okta with MuleSoft. So we can then protect our APIs with open ID connect.
Andrew Collins: And we'll also be looking at new security features like behaviors policies and web or thin. So we're very happy on how our journey has gone now with Okta. And we're looking forward to continuing our partnership with Okta and releasing all these new features.
Jade: That was awesome. So thank you so much Andrew and Cameron for talking through, how central are partnership with Monash and we've learned a lot as Okta partnering with on this experience. And I want to talk about security and user experience with Okta. So, we're all pretty familiar with kind of paradigm on security and user experience. And how you really think about it, and you've probably thought about this, when you are rolling out or designing a security flows for your end users.
Jade: But what we believe at Okta is if it's not usable, it is not secure. As I'm sure you can relate, just rolling out the factors is part of the journey, getting users to adopt, getting your users to understand is a whole change management flow that you have to continue. And when we think about building these secure user experiences, there's a lot of pillars that we, as a perk team play into consideration.
Jade: Setting up as appropriate levels to what your protecting. This steward across the flow so it doesn't hit the user all at once. And finally the responsibility between both the user and the system. A great analogy is for example, car safety. Although the user has upon the seatbelt, the car is also building with airbags to protect the user. And at Okta we care, we listen to our users a lot, our end users. We read and respond to every single review that they write.
Jade: We also proactively ask for feedback within the applications and the experience to see how could we make things better for them and hear from them and how they're using our product. And we're constantly looking at metrics and tracking product health, see adoption and success. And that feedback has been used to guide every chapter of the user journey from adoption to signing in, giving them controls to manage their security. And of course the core of why they're even here in the first place, accessing the applications they need, where they get the most productive work done.
Jade: So I want to highlight some roadmap items, our coming highlights this year, which we've want, and also partnered with on Monash. So, Monash did an amazing job on writing documentation and FAQ and helping with end users understanding why Okta, helping end users understand Okta and why it's used and we're currently, and some of our customers have done amazing work on this as well. So we are rolling out a new end user adoption tool kit with customizable templates, FAQs and information for you to adopt. Not only rolling out Okta for the first but also new features and products that you want to release in your organization and simplifying that for you.
Jade: On signing in, we currently have in beta, the passwordly experience. Helping users to not only have a more delightful experience of not having to enter passwords but also using more secure, like a better security flow using factors like Okta verify or Ubikey as a way to verify their identity and their device. Also, the experience of needing to reset the FMA. So there were examples where students would leave their device at home and they needed to reset it, but they're in the middle of an exam or they need to, or they're rushing to a, a class. And they need to really quickly access that information they need. So we are introducing, we'll be introducing soon, the ability to defer factor enrollment. Giving you the admin, the control to push out the, giving a grace period to the users to be at, for when they need to enroll in their factors.
Jade: Finally, also, what can users do right now if they do see something on their accounts that they don't recognize? What kind of controls do user have to protect their identity and your data. Well we are, right now in beta this ability for you to, for any users to be able report suspicious activities such an usual logins, password reset flows that they don't recognize. Or MFA enrollment they don't recognize. Which will give you also the admin ability to respond quickly and lock down and automate the response to protect your data. Finally, we when we think about when users are actually using these products to SSO, we are working, we are really investing in usability.
Jade: On the devices that they use. So on mobile we are redesigning the sign in flow with Okta mobile, using the sign in widget. So users can now MFA on the go, and can also SSO on the go. And also use it to self service unlock and reset their passwords, having a one stop shop to take care of their Okta needs. And for some users who do use the Okta dashboard, were all pretty familiar with this dashboard page that we love and know very well. So this year we actually are investing in a new end user design all together. We will be more modern, intuitive, responsive and accessible.
Jade: So, there's a lot coming on this roadmap that we've learned and discovered partnering with our customers like Monash. Understanding their user needs, understanding what they're going through and trying to partner together to make it better. So, if some of these features really interest you we'd love to have your feedback, go to this QR code or go this link and leave your details and also if your interested in seeing the demo that we'd like to have shown you, please leave your details and we can contact you afterwards to share that information.
Jade: So, without much, I would like to invite Andrew and Cameron back on stage to open the floor to any Q&A. There are mics being passed around right now so please if you get a mic, put your hand up and also stand up so we can see you better.
Speaker 4: Hi, first congratulations on a job well done there, it seems maybe I can hire you to do it to my company. No, but seriously, I was a little disappointed in not seeing on the road map that challenge that you guys have to face head on with the, temporary codes. And as I'm wondering if you can elaborate more on that since we weren't able to see the video I think that's gonna be our biggest challenge. I know there's challenges in terms of hardware tokens, you know Ubikey and things like that for people who don't wanna use their phone, privacy concerns and things like that. But I think that is probably the biggest.
Cameron Duck: Okay, so what you would have seen in the video was, we're using the custom SAML factor that's currently in beta so it acts like any other factor but it goes off to a SAML application, so when the user enrolls, they're taken off to the application and they're presented with 10 one time use codes. They have the option to email those codes to themselves but to not a Monash university email account cause there's no point storing your codes in the account you need the codes your codes to get into.
Cameron Duck: They can print them out on a sheet of paper or they can save them as a text file. So I save mine as a text file, store it with my password vault, I have it there. So, if I've broken my phones or I replace my phones I no longer have that second factor, I go to log in, I go to the pull down to choose which factor I want to use, I can select the backout codes, the backup codes. Grab one of those ten codes, type em in, and I log in as per normal like it's another factor. That codes no longer usable so I've only got nine left, but because I've got in I can then reset the factor myself, enroll my new phone and I'm all good to go.
Speaker 5: Did you guys also roll out modern authentication and disabling things like imap and pop at the same time that you did MFA, is that still ahead for you or what does that look like?
Andrew Collins: Now I know at the same time, but we're in the process of working through that at the moment. Disabling that through Google.
Speaker 5: Thanks.
Speaker 6: Hey guys so with the common scenario of a, user losing or misplacing their device and they call up looking for help, how do you validate they are who they say they are?
Andrew Collins: Always a challenging one that one, I've actually got a really good diagram on my laptop. But, so there's a few things they need to go through and providing their data of birth, first name last name, things like that, student ID. We also have a mechanism as well to be able to send the user SMS, and then they read back that SMS code as well.
Cameron Duck: We also don't allow the same call to do a password and MFA reset in the one go because obviously if they've convinced a service desk person that they are who they say are and get both things reset, that's, can be a problem so, we try and restrict it to just I forgot my password, I still have my second factor, or my phone's broken but I still got my password. Only get one thing reset.
Speaker 7: How long did it take you it from the start of when you got Okta until you started that one day cut over on the log in.
Cameron Duck: So, we signed the contract with Okta three weeks before Oktane last year. Which if memory serves is about May. Their cut over day was the 28th of June. So yeah, there wasn't a huge amount of lead time. But yeah.
Speaker 8: Can you talk me or us through that custom accounts scenario where you said you could use Google indicator for multiple people but for one account?
Cameron Duck: Yep, so, like you said, we have accounts where multiple people do have to log into, because a couple of people do the same job and there's one account that they use, a central account, or things like that. So with an authenticator app and you can use Okta verify without the push an authenticator app, you're either give a qr code to scan or a code to type into. And if you save that QR code or the code you can type it and and then roll multiple phones at once. I know some of the areas have got everyone in the room same time they've done the enrollment, just scan, next one, scan, all the way through.
Jade: Question in the back.
Speaker 9: Yeah thanks, as a university you probably have a large number of new users showing up roughly the same time every year right? Yeah obviously looking forward to the differed enrollment feature I imagine but today what do you do, do you enroll them all on day one, do you stagger that somehow?
Cameron Duck: Okay so the, it's about the second or third week in January, is our very fun week. That's when the state of Victoria issues all of the university placements to all the students. So, the short answer is one one day we offer ten thousand places out, and if everyone's an eager student, they enroll at exactly the same time on that one day and we create ten thousand accounts. It normally happens over about a week but enrolling for MFA is just another step in the, in the enrollment process for the university. Click on your link, yes this is me, I wanna study medicine, I wanna do these classes, here's a, set my password, enroll in MFA, sign up for these clubs, do this task, do that. It's just another step in the enrollment process. So, all new users don't have a choice. It's just the thing they do after they set a password, they roll for MFA, have to do it the same as they have to set a password.
Speaker 10: Thanks, I work at a university also, were in the middle of our MFA rollout and one of the challenges we faced you mentioned people who either don't have a phone, don't wanna use their phone whatever, you distribute Ubikeys, we use OTP tokens, the challenge is how do you distribute those, your volume is a little bit greater then ours, distribution becomes a giant issue for us, I'm interested in what percentage of your users aren't using phones, they're for using Ubikeys in your case and how you get it to them.
Cameron Duck: Okay so, we currently have about 2000 keys in the world out of our 130000 enrolled users. So, while it's a large number, it's not a huge percentage.
Speaker 10: We're already getting that and we only have 5000
Cameron Duck: Yeah. So, we have an advantage of we have service centers, our desktop support guys are spread out across the university, across all the campuses, across all the locations. So we just use our internal mode from our central store which also does all the laptops and the desktops and stuff like that. It's just another item, like you want a new monitor, gets sent out to the local service center. And they either just drop the key off to the user or help them enroll in that.
Speaker 10: What about people of campus, because that's hard to consider, you have to factor in the foreign countries and stuff. How do you get em a key?
Cameron Duck: So for the ones that are that wide ranging and, I'd know of a couple of jobs we had of people over hear in the US, someone in Sweden we were dealing with and that sort of thing. We just use the post.
Speaker 10: You trust it?
Cameron Duck: They still have to enroll the device, they still have to log in, so it's no less secure then it is before MFA. So, yeah, that the best way we can do it, we had a bigger problem with people while rolling out traveling. Where they weren't in the same location for more than a couple of days and how do we get their key to them. So we had a process where we could, where we'd defer, enforcing them for MFA and told. Yeah they'd contact us, go I go the email, but I can't be.
Cameron Duck: This is your one.
Speaker 11: One for you Jade. Can we access the passwordless experience in the new portal now or do we have to wait?
Jade: That's currently in beta, it will be coming out in EA, hopefully by the beginning of H2.
Speaker 11: If we're in the beta program we can access it now?
Jade: Sorry?
Speaker 11: If we get in the beta program we could access it now?
Jade: You can access it now yes, you can play around with it on your preview walls, once you go to early access, you'll be to configure it for your production for rollout.
Speaker 11: Thank you and one for you guys, what was the curliest problem you had along the way.
Cameron Duck: We had quite a few applications that were very old, and very handwritten, and very awful. That no one knew how they were configured so we had people having to go in and work out how the authentication with the app worked and we'd have to go and help them work out how to change these applications over. That and trying to schedule everything in such a short period of time because as you can imagine, our web easy at the time, though we an't do it at this time. But with the help that we had from the push from CIO and those sort of executives, we had the backing to, yeah force it.
Andrew Collins: Yeah definitely. We also engaged professional services from Okta as well. And they were able to help out with some of those applications like WS fed because it doesn't play nicely. And some open ID stuff as well.
Speaker 12: Can you speak more to how you get executive buy in on this, I also work at a university and we're really interested in rolling this but we have a lot of concerns about the effect it'll have on registration or faculty teaching day to day. So can you speak more to that?
Andrew Collins: Can you just repeat the question please, sorry.
Cameron Duck: We're used to you guys not understanding us but sometimes it's a little bit this way too.
Speaker 12: Sorry, how did you go about getting executive buy in. We have a lot of concerns about different kinds of users and how they'll react MFA so we're very interested in rolling it out but we don't have that executive buy in yet.
Andrew Collins: Yeah, well that was really easy because, one of our focuses at the university is cybersecurity. And, because of all these breaches happening all the time, our CIO, they just wanted it in. It was them who pretty much came to us to say hey guys you need to roll this out, by 2017 or, or something like that, or 2018. So we really didn't need to push them at all, that was more pushing us.
Cameron Duck: Especially when we, our CIO saw some of the attacks that we've been under like the silent librarian attack. And he was able to push the requirement back up the tree. And we actually enrolled our senior staff first. So they all saw the process, understood how it happened, understood why it happened. And then we'd have help from them to push it down to everyone else.
Jade: Also this thing you're trying to work through, please come talk to us after, talk to me afterwards, we can connect you some other customers who have been able to successfully do that.
Speaker 13: We probably have time for just one more question before we wrap up the session. If there aren't any other questions, thank you to our presenters, thank you for attending.
Jade: Again if you would like to see the demo, please contact us, leave details here and we can connect you with those resources. Let's have another round of applause for Andrew and Cameron.
Monash University's journey with Okta from choosing a solution to today, now one year into their partnership. They'll share the security challenges they faced prior to Okta and the roadblocks they encountered along the way. Plus, the solutions they crafted in order to migrate 200 applications in 34 days and roll out a diverse set of MFA factors to 100,000 users in only 100 days.
