Oktane19: A Path to Achieving Network Security ZEN
Transcript
Details
Salima Kaissi: Thanks all for coming. Welcome to this session A Path to Achieving Network Security ZEN. I believe by now you attended so many sessions and maybe you know by heart the Safe Harbor statement. My name is Salima Kaissi. I work with business development team here at Okta. I manage some of our strategic alliances such as the VMware ONE that we'll be talking about in today's session.
Salima Kaissi: Today I'm very excited to co-present in this session with Erik Anderson and Den Jones from the security team at Adobe. Today Eric and Den will show us that balancing security requirements with a pleasant user experience is not a challenge anymore. Adobe believes this is possible. They will share with us there's your trust framework for achieving this balance through their projects called ZEN.
Salima Kaissi: But before that I'll share with you an overview about Okta's vision versus Zero-Trust. In the old approach, security relies on a network perimeter. In this approach anything inside the perimeter is considered as trusted; and anything outside the perimeter is considered as entrusted, and this is where the bad guys live. This model is problematic because when the perimeter is breached an attacker has an easy access to almost all resources because of this trust model.
Salima Kaissi: Also because of the rise of mobile cloud, BYOD, you name it, the traditional perimeter is increasingly becoming difficult to enforce. In fact, there is no perimeter around your sensitive assets. Look at these slides. Customers, employees, partners are all trying to access different resources from different devices, different networks, and different locations representing potential threats. So the result is that we can no longer assume trust.
Salima Kaissi: In this new world where different users are accessing different data from different devices and locations and networks, the new reality is that people are the new perimeter and we need to take into account the context by which they are accessing data while we are making access decision.
Salima Kaissi: When people are the perimeter, identity becomes the foundation of a Zero-Trust strategy. Identity is this linchpin in the ecosystem and the one constant while everything around us is changing. Identity is the single control point across devices, networks and locations that organizations can use to set their security decisions. Identity, as you heard yesterday in our keynote, identity is the trust platform.
Salima Kaissi: That was in a nutshell our vision for the Zero-Trust, a vision we strengthened through our partnership with VMware. We have come together to offer advanced identity capabilities to digital workspace. By integrating VMware Workspace ONE with the Okta identity cloud, customers can now securely and easily move to the cloud, use the best of these technologies and simplify IT management.
Salima Kaissi: By combining industry leaders in identity and access management and unified and port management, we offer the Best-in-Class User Experience and the Best-in-Class Security while allowing customers to leverage any existing investments.
Salima Kaissi: One of the use cases we focus on in this integration and partnership is the contextual access management. Contextual access management is what really enable the Zero-Trust model. We've partnered with VMware to allow organizations to take advantage of both the user context and the device context
Salima Kaissi: So through Okta, organizations can assess the user, who is the user, which groups they are in, are they accessing from an address that we have not never seen before, which are they entitled to? VMware provides the device context, is this a managed device, is it a compliance, is it secured?
Salima Kaissi: Thanks to these context, we can issue a contextual response and decide whether we want to allow the customer to access directly if they are coming from a device that is managed and trusted by VMware or we decide to prompt them for a second factor to verify they are who they said they are. This form of contextual access really is enabling the Zero-Trust model.
Salima Kaissi: Now when we say there is no perimeter, applications are most of the time using passwords as the single security mechanism to separate malicious actors from the system. Look at these numbers, they are alarming: 81% of data breaches involve stolen or weak credentials, and 91% of phishing attacks target credentials.
Salima Kaissi: Let's face it, password management is really hard and most of the time we end up choosing the easy way out by duplicating passwords. Data show that almost 75% of passwords are duplicated. So users are not really making it any harder for attackers. In this new world, hackers don't break in, they log in.
Salima Kaissi: How can we start removing this password challenge? We do that based on trust signals from both Okta and VMware. For example, if a device is managed and trusted by VMware, a user can experience a one-touch access a model, a password list experience where a user only need to use their username to get access.
Salima Kaissi: But what about when a device is unmanaged? In this scenario, Okta can still assess the user based on the regular policies and we can still provide a password list experience through a push notification to mobile.
Salima Kaissi: This is how it works. The users would use their username, they will then get an Okta verify push notification on their mobile device, and that all they need to do is to tap to approve, and they are granted access.
Salima Kaissi: So that was an overview of our Zero-Trust strategy, how we strengthen this strategy through our partnership with VMware. Now I will hand it over to the Adobe team so they can share with us the Zero-Trust framework and how they use this integration in their ZEN projects.
Den Jones: Hello. Hey, folks. I'm Den Jones, Director of Enterprise Security for Adobe. We're privileged to be here and then we thank Okta for inviting us. We look at Zero-Trust similar to this and we've partnered with Okta and VMware along this journey. Where I say similar you'll see some differences in the slides that we will share. That safe harbor statement usually applies to things that are in the future.
Den Jones: We'll share things that we've done, delivered, got some war stories about, and happy to share with everyone else. The other thing we'd love to share is we do have open positions to join our team. We're looking for elite security architects, so a shameless plug for that. Then, we're also looking for someone to join our security and intelligence team. So if machine learning and UBA is a big thing, then Eric is looking for someone in that space.
Den Jones: Let's jump in. We'll explain a little bit about our view of Zero-Trust because I think everyone has a different perspective and our one is a little quirk here. As we like to say at Adobe, "So we'll do the Adobe way," right? Throughout history, we've always ignored the device, we've always said "Hey, I'll let you login. You're doing the authentication and then I will trust that that's you." The problem is you're coming in from five devices and all devices are different from a security posture and we ignored the device context, and we knew that was an issue.
Den Jones: We also knew the perimeter was not safe and for years we've always said, "Just because you're inside the corporate network it doesn't mean you're safe." It actually might be safer at home because your home may be less of a target. But your corporate identity is a huge target depending on the company and the industry you're in.
Den Jones: At that point, we also look at the tactics and techniques of the attackers. It was years and years ago they did a forced attack and they were trying to get into account that way. For some reason the industry thought, well, let's change our password every 90 days because we don't have any knowledge whether you were attacked or not so that's the longest you still have in an account. This whole thing changed when that was no longer how we're being attacked and we're just being socially engineered.
Den Jones: We recognized this is a big thing for us. This is really what was important. But let's define it. I mean, it's really the same how you here at Okta describe it. The security e-boundary has evolved. The authentication should be based on the user and device posture and then that we don't trust any network.
Den Jones: In fact, could you imagine a day where your office networks were just like Starbucks and the only thing you can do in that network is just get to the Internet, and that's the only thing you needed to do to do your job? This is the journey that we're on and we'll explain exactly where we are on this journey.
Den Jones: I think this clicker is also from 1974. Right.
Den Jones: We've done this talk a few times and we've always been questioned, "Well, wait a minute. Are you getting rid of firewalls?" No. We still have firewalls, they're still at the egress points. But what we're really doing is we're taking the application and we're making it internet accessible.
Den Jones: Those are legacy apps that are on-premise, and now you can get to them without the need to VPN in. So we've changed that security e-boundary. Then, as I mentioned, the authentication is based on user and device. We'll explain a little bit more. When the smart people come up, then they'll explain more.
Den Jones: The purpose for us ... If you can imagine we're talking to our C levels and our board and we're trying to explain this idea and this concept, we want to turn all the internal apps into a cloud-like state, we want to tell the users they no longer need to use VPN, and secure network level access based on device and user posture. So those are three big things.
Den Jones: What was really funny is the architect who sold me on the vision a few years ago, he listed 20 big things. I was like there's no way I can boil this down to an executive and say there's 20 wins. But if you look at the ZEN's top 20, we're covering eight of the top 20 just by going this one program. But I never had to once go to my boss and say, "Hey, we're doing the ZEN thing," because that never goes down well.
Den Jones: Before we hand over to Eric, I want to talk about leveraging existing investments. This is really, really important to us. If you're an Okta customer today or you're thinking about becoming one and the Zero-Trust thing is really attractive to you, we can tell you that because we are an Okta customer, because we are a VMware customer, and because we're an F5 customer and a Splunk customer, all we had to do was talk to these companies and say, "Hey, do you want to work together with us on this?"
Den Jones: The first about was Okta and VMware their engineering teams come into help us connect these things together so that we could use VMware to get the device context and we can do Okta to use that information and get the user context.
Den Jones: When you think about cost of this, I know you may have read about Google's BeyondCorp and they're seven years in and there are millions of dollars, we are one year in on production and we're $240,000 and we increased our staff by one. So to say you cannot do it or to say it's hard, I think maybe you're thinking about another way, but we've done it unless the quarter of a million in one year and we had one more person joined the team.
Den Jones: I can step back at that and let Eric tells you how we done it, and then at the end we'll share a little bit more details. You'll realize that it's not a real big stretch to get there. We hear people talking about password lists. Well, we're using stairs instead of passwords. So this week with our security intelligence team we've removed the need to change your passwords every 90 days for 16,000 people. So 16,000 people times every 90 days, 15 minutes of frustration and hitting your head off a wall, we go about 46,000 hours of savings, or employee frustration is what I like to think of this.
Den Jones: It's possible, if you've got investments, it doesn't matter who your EDR is, it doesn't matter who your MDM solution is, you can connect these things. I'm gonna hand it over to Eric and he'll explain the magic.
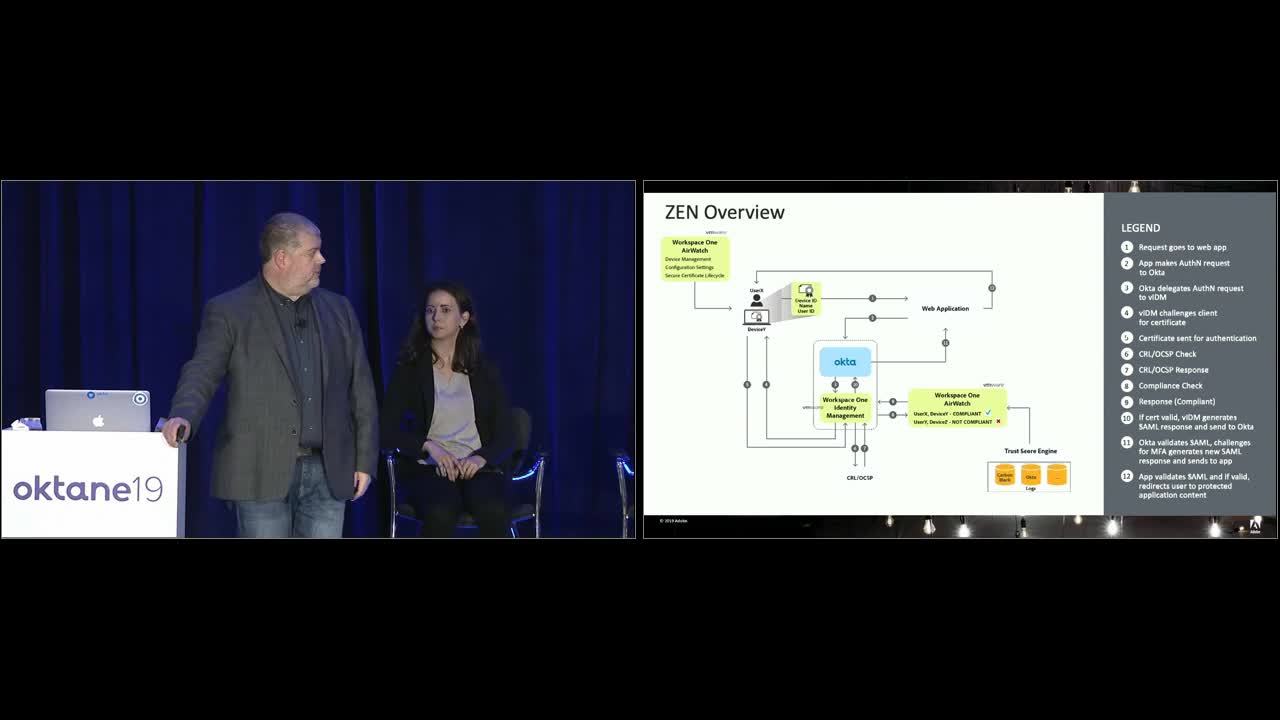
Eric Anderson: I'll try. Thank you everybody. I'm gonna attempt to show you some architecture designs on how we implemented it. The first one I'm going to show you is our implementation for applications that are on premise and exposing them through the proxy. Now I'd like to walk you through, and kind of give you a chance to take a look at it, we're gonna start on the left side looking at the users. As Den described, all of our users have VMware's AirWatch installed on their managed devices. With the AirWatch product, we're able to push down a ZEN certificate that has a footprint of the device itself and is also associated with that user name.
Eric Anderson: For the applications that are exposed out through the proxy, when they go to those URLs which are exposed through a DNS proxy, so they go to the same URL, whether they're on-premise or sitting at Starbucks, it will walk them through the access policy engine, which is using F5 and their APMS, and it will check to see if a Zen certificate exists on their system. If it doesn't, it will just automatically say, "You don't have access. You need to be on premise to access this without a ZEN certificate." At least that's how we're our initial rollout has been.
Eric Anderson: If we do detect the ZEN certificate on your machine, it will then walk you through an Okta login process. As Den had described, with Okta, what we've done is we've leveraged the ... I forget what it's ... The Okta dynamic identity engine to come in and say, "Hey, there's a cert here. We're gonna hand it off to vIDM," which is the VMware identity management tool, and it will use the ZEN certificate as the replacement for username and password.
Eric Anderson: As part of that process going through vIDM, it does reach out to AirWatch, checks to see if the device is compliant. That's where it ties into what we were talking a little bit earlier about with Splunk and the security intelligence team. We're looking at user behavior and user logs and authentication logs. We will set the compliant flag and AirWatch based on what we see in the patterns and usage of the users. Assuming that the device is set as compliant, vIDM will create a same old response, go back to Okta, and then prompt them for the MFA. Then they can continue in and go on their merry way with the application.
Eric Anderson: The second one I wanted to show you, kind of this next one is the same workflow but it's showing just the regular authentication flow. Whether the application is on-premise and going through the proxy or if this is a SaaS based application, we're using the same workflow where we have the AirWatch installed on the same device.
Eric Anderson: In this case, they will hit the application URL. Say, it's workday or concur other applications we all used to, that will go to Okta and an Okta will initiate the same authentication workflow. It will hand it off to vIDM. It will verify if there's a ZEN certificate. If it's present, it will use that for authentication.
Eric Anderson: But the difference here is, if there is no ZEN certificate, it will fall back to normal Okta authentication. So it'll fall back. If it doesn't see the cert, it'll prompt you for the good old-fashioned username and password before it lets you go in and then do the MFA prompt.
Eric Anderson: Then the great thing about both of these architectures is we were able to implement those across ... Well, let me show you the next slide before I say this. We were able to deploy this across 2,000 applications that we have in production in Okta without requiring any interaction from the application administrators.
Eric Anderson: This was all done through the Okta admin console and leveraging the backend of Okta. We were able to take these applications along for the ride and now it's the default workflow. Any application that's a SaaS based they are on-boarded through the ZEN process. As you can see, we've got over 42,000 devices set up using AirWatch and managed devices with over 30 applications that we've exposed through this proxy process.
Eric Anderson: The Trust Score Engine, we touched on a little bit, that's an engine that we have a security intelligence team that's analyzing logs through Splunk, through machine learning, and taking that intelligence and reaching out to customers. Much like you've probably seen when you login to Yahoo or other apps that says, "Hey, is this you? Have you done this before?" We're doing that very same thing internally looking at behavior across different types of applications. We then will feed that back into AirWatch to help define and set compliance flags.
Eric Anderson: What our hope is that as we develop that and make it and get deeper and further into our project here, version 2.0, so to speak, we'll be able to then start dialing up the trust of different applications. So based on the trust score of your device, maybe the restrictiveness of an application, we can then decide, based on your device score, we're not going to let you in this device. Then we're also obviously partnering with Okta and leveraging their capabilities to augment and take advantage of what they can see.
Eric Anderson: I thought I'd show you real quick, here's an example of what a user experience is for a compliant device. This is going to our internal Wiki. But imagine you're sitting at a Starbucks-
Den Jones: Maybe in Peet's
Eric Anderson: Excuse me?
Den Jones: Peet's, let's get to that.
Eric Anderson: Peet's is okay. I'll take it just in case. We're showing you the certificate here as installed. Through AirWatch we have pushed down a little bit of code to suppress the certificate for the user. But here we wanted to show that it's being presented. But a typical user does not see it. Here you see: vIDM is validating a certificate, MFA prompt. This is much faster than the demo is for everyday corporate experience. We've kind of slowed it down a little bit so you can see it. Then, now they're in the Wiki just like they would be whether they're sitting at their desk in the office.
Eric Anderson: Then I can show you the last demo we've got, is a non compliant device. This is the experience of the same person sitting at Starbucks, or Peet's, if it's got to be Peet's, and their device does not have the ZEN certificate and they're trying to get to the same site. They'll just be presented with that. That went by really fast there. It just tells them access is denied.
Eric Anderson: We have the capability to customize that and dialed up. As we get deeper into this maybe this application, depending on your trust score, we may say, "We see you every day from this Peet's logging in here. It's normal behavior maybe we'll let you in as you go."
Den Jones: Eric, can we pause there for one second?
Eric Anderson: Yeah.
Den Jones: One thing I'd love to share, because I know we've got time because the clock says we've lots of time, so this link here talks about your trust score to view and improve it. One of the things that we've done was, so when I headed the team my predecessors were pushing what they called an ASDE. It's like a secure device, right?
Eric Anderson: Right.
Den Jones: Everyone's workstation must have all this stuff. Some pure IT team had to go out and beat people up and argue whether you should have malware protection or not. What would end up happening with the engineering teams is they'd be like, "No. For our business we're trying to run and build code and the malware thing slows us down. We want to remove it so we can do our job."
Den Jones: The problem is with that argument it was a circular argument of VP, VP, VP. Then in the end, the IT guy would get told to take it off and then they'd go in their merry way. My feeling is when you say security is everyone's responsibility, but the IT security team then behaves like it does, then we're not following through in those words.
Den Jones: What we've done was we build a device management portal that would allow you to opt out of things. So we give you a device that's got all the magic and the wizardry on it and if you decide for your business reasons you want to take off something, then go to it. We don't care. But what we will do is we'll give you a trust score. So when we broke built our first trust score engine, it would take static information, give you a score, and then roll that all the way up to CEO.
Den Jones: Now what we've done is we have got aggregated scores all the way to our boss and they can look at their directs and say, "Why is your team got a lower score than your team?" Then what we've done was we made that so that they can see all their peers' scores. And then, game on, right? When they wanna opt in or out of stuff, we're like, "We don't care." You and the business risk, we've said all along, but now we're behaving in that way.
Den Jones: Then the other thing with this, which was really impressive what the team done, was when you've got, we're still mid-flight, right? So we've got 42,000 devices that use this, but we know we've got about 40,000 that don't. But now what we know is we just need to click one box and say you can only access these apps from a compliant device.
Den Jones: Now what we've done is we've got capabilities that we can go back to our board with and say, "How about if you're gonna work day we just check the box now, we'll tell them you must have a ZEN enabled device with all the stuff and you can't get to work day without it and not even argue about it?" Then there's maybe some other apps or maybe engineering heavy where the argument might be a little trickier. So we'll get to that one later.
Den Jones: The other thing we're doing on the 40,000 devices that don't have MDM, when you log in via the system, we're scraping your information. We've not started this yet, but we're gonna start to inject that into the device management portal and give you a crap score. Because the bottom line is, we don't know it's your device but you're the one that just logged in with it, so you own it until you can tell us otherwise, and you're gonna get a shitty score so that it rolls all the way up to your boss's boss and they can explain it.
Den Jones: So the real thing here is we'll now find a way to know what's on your network, and know what we're doing with devices, and know where they're going because it all comes through Okta. We've got so many apps on Okta. We probably have 5 that are not and 2,000 or 1,800 there are. So the reality is, is you can't do any business or job in Adobe without logging into Okta to enable that. So we're really trying to get the full end-to-end ecosystem.
Den Jones: Then the other thing is because we've done this and then all this is so raise your hand if you change your password. You guys, I shared this earlier, right? We're now getting people complaining because they're not ZEN enabled and they still have to change their password. So we're like, well, it's a choice, right?
Den Jones: So the thing for us is, it's a really easy way to start to control and dangle so many carrots for your users that they want to do the right thing. If you make it easier for them to do the right thing, and we're more secure but we're less friction, which is really very rare in our business that we get to say that we've done that.
Eric Anderson: Did you want to talk about the what we're gonna do with the proxy enforcing even whether you're on premise to go through the proxy?
Den Jones: Yeah. We're year one into the journey. I always think of it being year one and a half, but we're going along our merry way. This is a year where we're going to do two big steps. One is, even when you're on premise, you're going to go via that proxy before you get to any app, and that gives us more control and more capability. This is also the year where we're gonna get heavy with NAC and start to block all access to data centers, unless you're going via bastion host and you have a ZEN enrolled device.
Den Jones: Then the other thing we're gonna do is we're planning this year to execute next year, but we're gonna live in the east-west traffic. So even though you've got an office subnet, the need for me to get to his laptop is really slim. So if I put self-service, I got to get ... I always made fun of because I build portals every week, I think. But, yeah, again via another portal you're gonna be able to register and say, "I want this device to talk to this device because I'm doing it for my business."
Den Jones: But ideally, almost all of that is inside lab space or in controlled environments, so it's not a common thing. But if we enable self-service to self-register, we've got high confidence that the only thing you need to do is have your device get to the internet and you don't need to talk to any other device on the network, and any app or service or capability you'd need to talk to would be ZEN enabled and that's how you'll get to is from the internet.
Den Jones: So it's kind of exciting because we don't know many people that have been that brave to pull that trigger yet. But we'll see how that flies.
Eric Anderson: Then, here's some resources that are available to you. We have done a white paper on this whole topic that we'd love you to go check out. Our contact information is in there too. We're happy to talk to anybody about what we've done and share war stories, share tips and tricks, and then-
Den Jones: Q&A.
Eric Anderson: Do we still have more time with that? There you go. Then I'm gonna hand it back to Salima to wrap it up.
Salima Kaissi: Thank you very much, Eric and Den. Last year, in Oktane, we announced a partnership with VMware and since that, not only we shipped to production all what we promised, but we also had customers that's already deployed such as Adobe and we're very excited about that.
Salima Kaissi: Before opening up to the questions, I would like to leave you with three main takeaways. First identity is the foundation of Zero-Trust strategy, and in fact it is a trust platform. Second, if we would like to get the best of bread technologies, integration is the key. That's the reason we built 6,000 plus out-of-the-box integrations and our objective is to get infinite integrations with all the services and products that we announced in Oktane, such as Okta hooks and workflows. Last but not least, I know Okta and VMware pride themselves on listening to customer feedback. This is a great example where we work together with the joint customers, such as Adobe. We listen to their feedback and we deliver the best results. So keep the feedback coming.
Salima Kaissi: With that, thank you very much. Please let us know if you have any questions.
Audience: Thank you. Question, you seemed to get that score, that risk score for each device. Is it only AirWatch or is it something else?
Eric Anderson: Right now the device trust score is based on whether you have things like carbon black installed or if you have obviously AirWatch carbon black and a couple other little pieces it's looking for. We're kind of in the emphasis state. It's more of a binary at this point where it's low medium or high depending on what you've got.
Eric Anderson: How do we check inside? AirWatch can provide us information as well as carbon black and can provide us information on the device itself and we write all that data into Splunk. So then we leverage Splunk and then we have part of my team that does the security intelligence work and they are applying machine learning across that and looking for that information. Then we're working on some weighted scores and things like that to really make the score a little more accurate.
Audience: How do you handle temporary contractors and vendors if they need to get to an app for support or something like that? Do they have to have like an internal account, do they have to have an internal machine? How do you do that?
Den Jones: That's an awesome question.
Eric Anderson: Do you wanna-
Den Jones: It's easy. Yeah, I'll take it. Yeah. The biggest problem you have when it comes to vendors and contractors is legally you may not be allowed to put your software on their machine. You may also not want to do that because it costs you more money. So our first hit is this year vendors will still be VPNing if they need.
Den Jones: But we have a bigger problem in an industry where vendors, and especially if they move on the high ray of coming and going, you can't live like that. So we're looking at other solutions like DAS where we'll get cloud services desktops they'll be ZEN enabled and then they'll start to access that. Because at the same time the other problem with vendors is they may steal your stuff. I don't know if you like that, but we don't. So we're kind of thinking, "Wait a minute. If I just give a vendor the VPN access, I'd have no control over their device." Again I have no device context. so we'll look to make that investment.
Den Jones: But yeah, that's a gnarly one. The other one that we've not solved is Firefox and Android. We are working with Google and Android to improve that experience. It's all about how we manage the certificate that's really tricky. Then Firefox is much the same, they really locked us down to the point where it's really hard for us to make the user experience easy.
Den Jones: But what we wanted to do is not have pop-ups and crazy choices for the users that were engine-room stuff. We've just had to right now, "Hey, let's keep moving. Let's not worry about that. But we'll get to that." So this year, vendors, we have a strategy, we have pilots. Towards the end of the year, I think we're going to have a group of vendors start user stuff.
Audience: I had a question about the ZEN certificate that you're pushing to the devices. Is that the same certificate that AirWatch pushes down when you have an AirWatch managed, an MBM managed device? Is that the same certificate? Are you pushing a separate signed certificate down from your certificate authority? Then the last question is, are you doing SSL authentication as where the last step of the SSL, handshake, it's asking for the personal cert? Is that how you do it?
Den Jones: I don't know if you noticed at the start, my title would have said director, right? The engineer who worked on it, he's in Mexico on vacation, but we do have another one of our engineers in the room that will nod or shake if I start going like really bad here. Right?
Den Jones: We made a conscious choice to use a separate certificate for the ZEN program. Right? We didn't want to reuse the wireless certificate that we previously appreciated and stuff like that. I'm so good, right? On the handshake stuff, I'm not sure, but in a white paper I do think we described it, but, Chris, I think we are. Right? Yeah.
Den Jones: One of the things for us was, when we were doing all our security reviews we were looking at what security do you get from our VPN or Cisco ASA's today and the encryption and all that stuff. We're like, we need to ensure we don't go backward. So we need to have something equal or better than that. So all the communication, encryption, and all the same goodness that we had on VPN, we have that and then we have a little more.
Den Jones: I think if you see the white paper and if you've any questions, Chris over here will probably be able to tell you some very details.
Audience: I have a question what we're doing for MFA type of things. Is that you are planning to implement or just through a digital certificate you want to control all identity?
Den Jones: I'm sorry, I didn't catch it.
Audience: MFA. Are you doing anything for that?
Den Jones: Oh, yeah. We made the choice few years ago that everything's MFA. Yeah. So 2,000 DAPs or some high number, everything's MFA. But what we do want to do ... There's two things, you've got to work with your application teams because they set timeouts on when they expire stuff that forces the reauthentication back to Okta. We need them to do their re-auth every 15 minutes so that we then do a lookup again to check if our cert is still good.
Den Jones: We're not there yet. We're still doing the 12 or 24 hours. Some apps are 30 days and some are seven. So we need to start to really control that expedience otherwise we don't wanna throw a Caspian line but we don't want to get anything more complicated than we have to. But if the user leaves the company or they're under attack, we want to kill the sessions as quick as it can.
Den Jones: We do kill sessions when we suspect. When we do at the security intelligence team, they will actually kill your auto sessions. But that doesn't do anything if you'd already connected and the app is not going to prompt again for 30 days. Right? That's a tricky one that we're still trying to improve on.
Den Jones: Then there was one more question down here.
Audience: Excuse me. Kind of on the user experience side, 2,000 apps is a ton of apps, are your users going through the Okta portal, with vIDM portal, or are they just browsing to a site which triggers the authentication process?
Den Jones: They just browsed the site.
Eric Anderson: Yeah.
Den Jones: I mean, we actually never told our users about the Okta portal because they don't care. I mean, sorry. But they don't care. I did hear, there's a lot of confusion where Okta has talked about, "Hey, we're doing more context awareness. We're doing more intelligent stuff. We're getting more devices." Then some people begin to think that that means Okta are trying to become an MDM player, and they're not.
Den Jones: They wanna partner with the MDM player because the app store you get with Workspace ONE, it's a little icon on my computer and I can install some nice fat cloud apps, right? I mean, I could do web links as well for one, but we don't do that so often. So the reality is there's 2,000 of those websites. I have no idea how many of them get used every single day. We can run reports. We're starting to think of we've made it so self-servingly easy for you to register your app and SAML enable it and do all that stuff.
Den Jones: But we've got 2,000. That to me, and what you guys might think. that's a crazy high number. Clearly, not everyone is using them every single day. So we're gonna also start to self-servingly clean that number up. So as part of this activity will even look at that, but I don't think anyone knows all the URLs. Not all 2,000 anyway, right?
Audience: Related to his question, what are you doing about legacy apps?
Den Jones: Awesome.
Eric Anderson: Shut them down.
Den Jones: Shut them down, yeah. Yeah. Look, here's the thing. Right? If you wanna move forward, I heard someone talk about this yesterday at the conference, they were walking about, you know, he watched movie Tarzan swinging along in the jungle and he grabs a vine. How many of the old vines do you want to keep a hold of because you can't keep moving forward?
Den Jones: The thing I said to the team was I'm not looking for perfection. Eric will tell you I use the term good enough. Right? Is it good enough? I got to get good enough quicker than nowhere perfectly ever. So, legacy? Don't care. But we are meeting with the RSA team about their archer program and telling them we're not impressed with their authentication and we do beat people up that still wanna use legacy off protocols and stuff like that. So we're not slowing down our ZEN thing, but we know we need to white list access to those things from within the firewall until they're gone.
Den Jones: Now we may work with the Okta stuff as they know some products that you could take advantage of that cover that space. So that's another option.
Audience: Does that factor into the scoring that you guys use? So if someone's using a really old app that uses unsecured protocols, does that lower their score?
Den Jones: Not yet.
Eric Anderson: It will.
Den Jones: It will. In the future, yeah.
Eric Anderson: That's on the roadmap, yeah.
Den Jones: Also, never change your password, again that's compromise indicator. We only selected 16,000 people for a reason, 4,000 of the other people still have access to a directory. So we used sale point to replicate when you change a password and we don't trust their directory. Not because it's not our team that runs it, that would be mean, but it's because we don't trust their directory secure. Well, we think it is, but the problem being is they are using their passwords in a regular basis so we no longer trust passwords.
Den Jones: I think the big thing about legacy is you've got choices to make and if the choice will slow you down and not help you get broad, mass improvement, then stop stressing over it and just keep going. I've said that quite a few times. It's like if we don't focus on this and you try and broaden that scope, you'll never get it done.
Audience: How do you guard against somebody misplacing a unlocked ZEN-enabled device?
Eric Anderson: We shake them.
Den Jones: I had this conversation with someone yesterday actually, right? Don't over engineer your stuff because you're compensating for stupidity. Right? We just don't have time for that. We assume that will happen. The one thing that's interesting, we met with our security team a lot, right? So we've got pen tests and bug bounties and our ZEN platform has been tested as much as possible. The interesting thing and their findings was, well, if I get Mimi cats on your box and you leave your phone unlocked, and let's say they're gonna have to brag and they get its pin, I'm like, holy shit, how many if's have you got here?
Den Jones: The reality is, if you leave your device unlocked and someone does something bad with it, then, first of all, maybe we missed on the MDM thing where we worry about screen lock timeout and stuff. But tough. I mean, the big thing is, is maybe if that causes a lot of SaaS-based incidents then I'll worry about it. I think the big thing is I'm not going to spend a dime to solve a problem where I'm not spending a dime because it exists to begin with. Right?
Den Jones: I wanted the team to move fast and any time people ... Because that's a true use case, right? I'm like, okay, I'm not worrying about that one tonight or tomorrow.
Salima Kaissi: It's the end of the session. Thank you very much, Den and Eric.
Eric Anderson: Thank you.
Salima Kaissi: Thanks to all for coming to this session.
Balancing security requirements with a pleasant user experience is an ongoing challenge. As identity-based threats have multiplied over the years, user authentication has become complex, with second factor authentication like One Time Passwords (OTP), re-authentication multiple times a day, and extremely long a1phanUm&r1C passwords. Frustrated users try to minimize their pain by sharing passwords across multiple work and personal accounts, increasing their vulnerability as an unintended side effect. Is it possible, in these high-risk times, to provide a login experience that’s both highly secure and positive for users? Adobe believes this is possible, and we will share our Zero-Trust framework for achieving this balance through “ZEN.”
The ZEN (Zero-Trust Enterprise Network) project from Adobe is an initiative derived from best practices and principles of today’s numerous digital workspaces. With no single off-the-shelf solution to fully deliver on these principles today, ZEN is pioneering technologies and workflows that make the path to a zero-trust network both attainable and efficient.
